Cybersecurity journalism during wartime is one of the most dangerous parts of a journalist’s work. Earlier, war crimes included spying and espionage. In the digital age, it has been carried in the form of cyber espionage.
Cybersecurity Journalism during wartime may get the journalist tangled in criminal offenses after reporting their findings which may not align with the government, and gatekeepers, among others.
Cybersecurity journalists are expected to write in a way that a non-technical reader can understand what went into the cybercrime. This calls for a continuous effort to learn and collaborate with experts with knowledge about the technical aspects of cybercrimes.
While details hold a critical place in reporting cybercrimes related to war, it is expected to be clear about where to draw the line between sharing information and blurring content that may create terror among people.
War Cybercrimes Posing a Threat to Data and Lives
Due to technological advancement, war crimes have extended beyond the war zone to the digital infrastructure. Critical infrastructure which is the life-blood of nations has been targeted with online manipulation of controls posing a risk to lives.
Cyberespionage is another form of spying that is carried out online via hacking, phishing, and deploying malware. Besides state-sponsored cyberespionage, cyberattacks during wars have often been aimed at organizations from one of the warring nations.
This has been observed as part of civilian hacker activities that disrupt the websites of organizations that are based in nations that don’t support the nation they do.
Hacktivists feel, as they claim, a sense of responsibility in fighting for peace and the people, and so they announce cyberwars. They make claims to launch Distributed Denial of Service attacks, defacement attacks, and other forms of threat.
Cybersecurity journalists have been reporting cybercrimes that are evolving each day to keep governments, organizations, and people at large aware of threats.
Cyberattack Claims by Hackers Amid War
There has been a hike in cyberattack news circulating the media in the name of cyberwar by hacktivist groups supporting either Israel or Palestine. Several NATO nations and others supporting Ukraine in the Ukraine-Russia war have also grabbed the headlines.
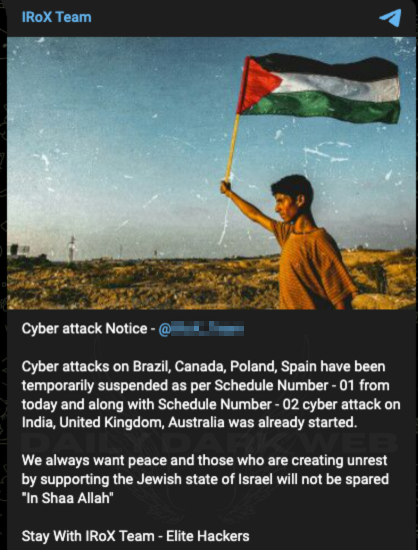
While hackers may claim they have infiltrated a system of an organization, can the cybersecurity journalist go ahead and report the incident as an attack?
When a cybercriminal makes claims, they may be doing so with the intent to gain popularity or make a standing in the underground world. This is also why verifying the claims is a prominent step to be followed by journalists.
A claim cannot be reported as an event that occurred without proof and must be reported as unverified announcements found on the respective platform. More so, cyberattacks launched in the name of war.
Reporting Cybercrimes Related to War and Sourcing Information
With social media and mobile phones, news no matter how critical reaches an individual as soon as the reporter hits the publish button. The speed aids quick dissemination of information.
However, with the ease of using Artificial Intelligence tools, deepfake technology, and, morphing images enormous fraudulent content has surfaced on social media. The task of filtering disinformation which involves false data from genuine news has gotten complex if not impossible.
One of the few sources people can turn to has been reduced to news media hence the onus to verify wartime news remains pivotal. This is while the government mulls over the credibility and fate of information shared on social media outlets including X, formerly, Twitter.
Free speech is a right of every individual and the media also enjoys the Freedom of the Press which allows them to express freely without interference from the state or the government.
This freedom comes with a great responsibility to share what they find accurate and not based on biases.
War poses threats that man may not ever be prepared to handle. While reporting war crimes, it is important for news media to report without compromising on ethics.
The code of ethics for journalists guides them toward publishing information that is accurate, fair, and thorough. While cybersecurity journalists are asked to be honest, and free from biases, they are also urged to be courageous in doing so.
Another requirement is for them to allow subjects of news coverage to respond to criticism or allegations of any wrong actions. They are allowed to gather information through undercover methods if it helps share the news completely and in full capacity.
While the media enjoys the pleasures of freedom in conducting research and unfolding truths, they are also expected not to intrude or engage in potentially harmful activities posing a risk to a source or the people.
However, just like most other laws that a nation follows, and another might not according to their own principles, journalistic ethics and freedom of the press have been curbed or modified by nations to their understanding.
Cybersecurity Journalism During Wartime and the Perils of Disinformation
In the middle of the Israel-Palestine war, people across the globe turned to social media to find artificially generated audio-visuals. Most of them included presidents of nations discussing topics around war.
According to a study, researchers found nearly 5,000 tweets circulated in seven months of 2022 which diluted trust among the masses. Addressing the Russo-Ukrainian war, the study found that Russian President Vladimir Putin and Ukrainian President Volodymyr Zelensky were shown doing things they did not in reality.
This resulted in creating fear among people in trusting information from any source. Knowing that there are artificial intelligence tools to create propaganda for people, they felt increasingly vulnerable in finding legitimacy in any content they found online.
Addressing the responsibility of cybersecurity journalism during wartime, a researcher who was part of the study wrote, “News coverage of deepfakes needs to focus on educating people on what deepfakes are, what their potential is, and both what their current capabilities are and how they will evolve in the coming years.”
Changing Threat Landscape and Cybersecurity Journalism During Wartime

The Australian Alliance of the Media, Entertainment, and Arts Alliance (MEAA), in a recent media release, addressed the killing of journalists who were covering the Israel-Hamas attacks.
The MEAA wrote, “They (journalists) play a crucial role as the eyes and ears of the world in reporting and explaining what is happening on the war front, including exposing war crimes.”
This was in response to the killing of nearly 24 media workers in Gaza who were covering the Israel-Hamas attack which began on October 7, 2023.
War coverage is neither easy nor safe for media personnel who stand amid war zones and lose lives. It is different for cybersecurity journalists who cover cyberattacks arising from wars.
The changing threat landscape has led to an increase in cyberattacks that lead to data breaches, identity theft, and stealing classified data. While more sophisticated cybercriminal groups breach the most secured digital infrastructure using AI, civilian hackers disrupt services through DDoS attacks or defacement attacks.
Chatbots like ChatGPT have made it easier for cybercriminals to find code to create malware. AI can be confused which threat actors take advantage of. This when used for cyberattacks needs to be prevented with technology that is also at par and can surpass the attack vector.
Several infosec media have been tackling cybersecurity news which requires extended technical knowledge. While offensive developers work on creating more evasive malware, cybersecurity journalists rely on self-learning, their IT teams, cybersecurity courses, and more to update their knowledge and do justice to their reporting.
To make the wartime news report complete for readers from all walks of life, cybersecurity reporters need to make sure they understand what may be portrayed by cybercriminals in their dark web posts.
This involves outlining the consequences of cyberattacks during war, the kinds of cybercrimes and their impact on data, and the potential misuse of data on them.
Cybercriminals Contacting Cybersecurity Journalists
Cybercriminals have been reaching out to reporters to spread their cyberattack claims and have also gone ahead and given interviews to reporters.
This makes way for gaining information about cybercriminal activities. However, it also poses a risk to the security of cybersecurity journalists. If hackers can gain access to the most secured infrastructure built on sophisticated tools and software, infiltrating the device of a cybersecurity journalist might be a minuscule task.
While cybersecurity journalists have the power to share information around the globe in seconds, they also have the responsibility to share factual and neutral information. This especially holds true when it comes to wartime cyber journalism.
Cybersecurity professionals and law enforcement agencies are still on their toes trying to reach people from every corner of the world about cybercrime. This shows the gravity of cyberwars which are growing steadily.
Cybersecurity journalism is the bridge between people, government, and cybercriminal activities that helps in the dissemination of information. If the mission of making people cyber-aware misses the mission of a cybersecurity journalist, their work may not bear results.
Just like reporting any news, cybersecurity reporters covering cybercrime during the war are to avoid sensationalism and not propel people to act in a certain way that they deem appropriate.
Technology has made reporting and forming content several times easier. However, no technology can beat the way a journalist can verify facts and provide unbiased information.
Media Disclaimer: This report is based on internal and external research obtained, through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.