The internet has become an integral part of modern society, yet its underlying workings remain little understood by many. A globally distributed communication network first emerged in the late 1960s through pioneering research in data transmission and packet switching.
Over subsequent decades, innovations in hardware, software, and networking protocols gave rise to today’s sophisticated yet user-friendly manifestation of the original concept. There are more than 5.47 billion active Internet users.
This post seeks to provide a comprehensive yet accessible overview of what constitutes the Internet, how it functions at a basic technical level, its key uses and advantages, as well as some disadvantages to consider. By shedding light on the Internet’s origins and operating principles, we aim to promote broader comprehension of this ubiquitous technology upon which so many now depend.
What is Internet?
The internet serves as a vast interconnected network of devices including computers, servers, smartphones, and smart appliances. Through the utilization of the Transmission Control Protocol (TCP) standard, these devices communicate swiftly to exchange information, files, and various services.
Functioning as a global hub of computer networks, the Internet facilitates data exchange among users across different workstations, provided they have authorization. This enables seamless interaction and collaboration among users utilizing diverse computing systems.
The infrastructure of the internet encompasses a range of components, including optical fiber data transmission cables, copper wires, and various networking infrastructures like Local Area Networks, Wide Area Networks, and Metropolitan Area Networks (MAN).
Additionally, wireless technologies such as 4G, 5G, and WiFi often require physical installations akin to traditional cable setups for internet access.
Control over the Internet and its associated technologies, such as IP addresses, lies with organizations like the Internet Corporation for Assigned Names and Numbers (ICANN), headquartered in the United States. This regulatory body holds the main role in overseeing and managing the internet’s functionality and addressing global internet-related concerns.
History of Internet
The inception of the internet traces back to ARPANET, conceived by the Advanced Research Projects Agency (ARPA) of the U.S. government in 1969. Originally, ARPANET aimed to establish a network facilitating communication between research computers across different institutions.
This innovative network design enabled continued operation even in the event of disruptions caused by military strikes or other unforeseen calamities.
ARPANET pioneered the utilization of packet-switching technology, revolutionizing computer interactions by enabling cost-effective and interactive communication.
Packet switching facilitated the transmission of data in small bursts, known as packets, which could independently traverse various network routes to reach their destination.
Unlike conventional voice services, this method did not necessitate a dedicated connection between users, enhancing efficiency and reliability.
During the 1970s, corporate packet networks emerged, primarily focused on facilitating access to distant computers through specialized terminals. These networks replaced expensive long-distance modem connections with virtual lines via packet networks, ushering in a new era of efficient data exchange.
Today, the internet stands as a globally accessible and collaborative platform, serving as a vital resource for millions worldwide.
It serves as the primary source of information and connectivity for countless individuals, fostering community development through social networking and content sharing. Additionally, private iterations of the internet cater to the needs of large organizations, ensuring secure and regulated information exchange within their networks.
How Does the Internet Work?
The internet operates through a complex network of clients and servers. Clients, such as laptops, directly connect to the internet, while servers, large computers storing websites, are indirectly connected. Servers are linked to the Internet via Internet Service Providers (ISPs) and identified by IP addresses.
Each website has a domain name for easy access, as remembering numerical IP addresses is impractical. When a domain name is entered into a browser’s search bar, the request is sent to a server, which translates the domain name into an IP address and uses a Domain Name Server (DNS) – akin to finding someone’s Aadhaar number in a directory. Once the IP address is obtained, the browser forwards the request to the corresponding server.
The server processes the request, displaying the website content requested by the client. For users on wireless internet, data travels through optical cables to towers, then to devices via electromagnetic waves.
Routers facilitate the conversion of light-induced signals to electrical ones, ultimately delivering internet data through ethernet cables to computers.
Types of Internet
Types of Internet connections vary in speed, efficiency, and technology. Here’s a breakdown of the primary types available:
1) Dial-up connection:
Utilizing a phone line, dial-up connections are slow and outdated. This method, recognizable by its distinct modem tones, was once common but is now obsolete.
2) DSL (Digital Subscriber Line):
Ten times faster than dial-up, DSL uses a modem to connect to the Internet, offering improved speed and efficiency.
3) ISDN (Integrated Services Digital Network):
More versatile than DSL, ISDN connects various devices like computers, fax machines, and phone lines. It allows the transfer of video, audio, and other data while maintaining phone functionality.
4) Cable modem:
This type of Internet connection links a modem to a television cable provider’s network, offering fast and reliable connectivity.
Wireless (WiFi): WiFi is the most popular connection method today, seamlessly connecting laptops, smartphones, and other digital devices via radio frequencies.
5) Broadband:
Known for its high-speed capabilities, broadband offers transfer rates of up to 100Mbps. Actual speeds may vary based on cable types, such as coaxial or fiber optics.
6) Cellular:
Provided by mobile phone companies, cellular Internet utilizes 3G, 4G, and 5G technologies. While 3G is being phased out, 4G and 5G connections offer fast and reliable mobile Internet access.
Uses of Internet
The internet serves a multitude of purposes and has become an integral part of modern life. Here are some of its primary uses:
- Communication: The internet enables instant communication through email, messaging apps, social media apps & video conferencing tools. People can connect with others globally, facilitating personal and professional interactions.
- Information Access: The internet provides access to vast amounts of information on virtually any topic. Users can search for news, research articles, educational resources, tutorials, and more, making knowledge readily available at their fingertips.
- Entertainment: From streaming movies & TV shows to listening to music and playing online games, the internet offers a plethora of entertainment options. Video-sharing platforms, online gaming communities, and digital content providers cater to diverse interests and preferences.
- E-commerce: Online shopping has revolutionized retail, allowing consumers to scroll and buy products and services from the comfort of their homes. E-commerce platforms offer many products, competitive prices, and convenient delivery options, enhancing the shopping experience.
- Education: The internet has transformed the field of education, giving access to online courses, virtual classrooms, educational websites, and digital libraries. Students can learn new skills, pursue academic degrees, and access educational resources; and when deadlines loom, many simply search write college essay for me to find professional assistance that helps them keep up with demanding coursework.
- Research and Collaboration: Researchers, academics, and professionals use the internet for collaborative projects, data sharing, and research collaboration. Online databases, academic journals, and collaborative platforms facilitate knowledge exchange and collaboration across disciplines.
- Work and Productivity: With the rise of remote work and digital nomadism, the internet has become essential for conducting business operations, collaborating with colleagues, and accessing work-related tools and resources. Cloud-based productivity suites, project management platforms, and communication tools streamline workflows and enhance productivity.
- Social Networking: Social media platforms enable users to connect with friends, family, & acquaintances, share updates, pictures, and videos, and participate in online communities. Social networking sites have become integral to social interaction, networking, and staying connected with others.
Internet plays a crucial role in various aspects of daily life, facilitating communication, information access, entertainment, commerce, education, research, and productivity. Its widespread use continues to shape and redefine how people interact, work, learn, and entertain themselves in the digital age.
There Are 30 General Search Engines in the World
- Google:
- History: Founded in 1998 by Larry Page and Sergey Brin.
- Location: Based in Mountain View, California, USA.
- Daily Searches: Over 5 billion.
- Bing:
- History: Launched in 2009 by Microsoft.
- Location: Headquarters in Redmond, Washington, USA.
- Daily Searches: Over 1 billion.
- Yahoo!:
- History: Founded in 1994 by Jerry Yang and David Filo.
- Location: Based in Sunnyvale, California, USA.
- Daily Searches: Around 350 million.
- Baidu:
- History: Established in 2000 by Robin Li and Eric Xu.
- Location: Headquarters in Beijing, China.
- Daily Searches: Over 1 billion.
- Yandex:
- History: Founded in 1997 by Arkady Volozh and Ilya Segalovich.
- Location: Based in Moscow, Russia.
- Daily Searches: Over 150 million.
- DuckDuckGo:
- History: Founded in 2008 by Gabriel Weinberg.
- Location: Headquarters in Paoli, Pennsylvania, USA.
- Daily Searches: Over 100 million.
- Ask.com:
- History: Originally known as Ask Jeeves, founded in 1996.
- Location: Based in Oakland, California, USA.
- Daily Searches: Around 100 million.
- AOL Search:
- History: Founded in 1995 as America Online.
- Location: Headquarters in New York City, USA.
- Daily Searches: Approximately 20 million.
- Ecosia:
- History: Founded in 2009 by Christian Kroll.
- Location: Based in Berlin, Germany.
- Daily Searches: Over 15 million.
- StartPage:
- History: Founded in 2006 by David Bodnick and Ixquick.
- Location: Headquarters in New York City, USA.
- Daily Searches: Around 5 million.
- Swisscows:
- History: Founded in 2014 by Andreas Wiebe.
- Location: Based in Switzerland.
- Daily Searches: Over 1 million.
- Gibiru:
- History: Launched in 2009.
- Location: Headquarters in Denver, Colorado, USA.
- Daily Searches: Approximately 100,000.
- Mojeek:
- History: Founded in 2004 by Marc Smith.
- Location: Based in Brighton, United Kingdom.
- Daily Searches: Around 10,000.
- WolframAlpha:
- History: Developed by Wolfram Research.
- Location: Headquarters in Champaign, Illinois, USA.
- Daily Searches: Over 1 million.
- Yippy:
- History: Formerly known as Clusty, founded in 2004.
- Location: Based in Fort Myers, Florida, USA.
- Daily Searches: Approximately 100,000.
- GigaBlast:
- History: Launched in 2000 by Matt Wells.
- Location: Headquarters in Albuquerque, New Mexico, USA.
- Daily Searches: Around 500,000.
- CC Search:
- History: Launched by Creative Commons in 2019.
- Location: Based in Mountain View, California, USA.
- Daily Searches: Approximately 50,000.
- Internet Archive Search:
- History: Developed by the Internet Archive.
- Location: Headquarters in San Francisco, California, USA.
- Daily Searches: Over 100,000.
- Gibiru:
- History: Launched in 2009.
- Location: Headquarters in Denver, Colorado, USA.
- Daily Searches: Approximately 100,000.
- Boardreader:
- History: Founded in 2000 by Amir Blich.
- Location: Based in Seattle, Washington, USA.
- Daily Searches: Around 100,000.
- Search Encrypt:
- History: Launched in 2016.
- Location: Based in Cyprus.
- Daily Searches: Over 50,000.
- Qwant:
- History: Founded in 2013 by Jean-Manuel Rozan and Eric Léandri.
- Location: Based in Paris, France.
- Daily Searches: Around 10 million.
- Seznam:
- History: Founded in 1996 by Ivo Lukačovič.
- Location: Based in Prague, Czech Republic.
- Daily Searches: Over 30 million.
- Ekoru:
- History: Launched in 2020.
- Location: Based in Seychelles.
- Daily Searches: Data not publicly available.
- OneSearch:
- History: Launched in 2020 by Verizon Media.
- Location: Based in New York City, USA.
- Daily Searches: Data not publicly available.
- Givero:
- History: Founded in 2018.
- Location: Based in Copenhagen, Denmark.
- Daily Searches: Data not publicly available.
- Unbubble:
- History: Launched in 2017.
- Location: Based in Bonn, Germany.
- Daily Searches: Data not publicly available.
- Searx:
- History: Open-source metasearch engine.
- Location: Development community distributed worldwide.
- Daily Searches: Data not publicly available.
- MetaGer:
- History: Developed by SUMA e.V.
- Location: Based in Hanover, Germany.
- Daily Searches: Data not publicly available.
- Gigablast:
- History: Launched in 2000 by Matt Wells.
- Location: Headquarters in Albuquerque, New Mexico, USA.
- Daily Searches: Approximately 500,000.
Top AI Search Engines
Google: The word Google should not come as a surprise to anyone, since Google is one of (if not the) largest search engine on the planet. While early versions of search relied on traditional algorithms, Google has been more proactive at rolling machine-learning into search algorithms. Google has billions searches per day, an estimate is 5.
Bing: Redmond, Washington-based Microsoft makes Bing. Bing, on the other hand, is less famous than Google, but it too relies on various AI technologies to improve its search results, such as intelligent answers and image recognition. Bing processes millions of searches per day.
Yahoo: Yahoo Search isn’t used as much, being part of the greater Yahoo site, it utilizes AI and machine learning algorithms to supply the most relevant search results. First founded in 1994, Yahoo has certainly reached new heights with its search offerings, but it’s lost some of its lustre compared to Google and Bing. A large number of searches are processed on a daily basis.
Baidu: The”Google China.” Based in Beijing, Baidu is an undisputed leader in the country in the search engine space and has been more and more involved in a use of AI technologies among its services. Baidu – a search engine service with over a billion users, searches billions of times per day, mostly in China.
Yandex: Yandex is a Russian search engine based in Moscow, and currently the largest search engine in Russia and several other countries, such as Belarus, Kazakhstan and Turkey Powered by AI and machine learning, it responds search results uniquely, and manages millions of searches everyday.
DuckDuckGo: Based out of Paoli, Pennsylvania, DuckDuckGo sets itself apart by focusing on privacy, and not following your online activities. DuckDuckGo: Far smaller than Google in scale, but growing steadily and with millions of searches a day.
Advantages of the Internet
- Convenient Online Banking and Transactions: The Internet facilitates seamless money transfers through online banking systems, allowing for quick and secure transactions between accounts.
- Enhanced Education and Employment Opportunities: With access to online platforms like LinkedIn, individuals can explore a wider range of job opportunities and connect with potential employers. Freelancing has also flourished, providing a flexible source of income for many.
- Diverse Entertainment Options: The internet offers a plethora of entertainment choices, including music streaming, gaming, movie and web series streaming, podcasts, and educational content on platforms like YouTube.
- Emergence of New Job Roles: The rise of social media and digital products has created various job opportunities, such as digital marketing and social media management. Online businesses thrive due to the internet’s reach and accessibility.
- Seamless Communication: The internet has revolutionized communication by offering multiple channels such as email, WhatsApp, and Facebook for instant messaging. Voice and video calling enable virtual meetings and discussions, breaking down geographical barriers.
- Enhanced Comfort and Convenience: Online shopping allows individuals to purchase many products without leaving their homes, from stationery to clothing and personal items. Additionally, booking train and plane tickets online saves time and effort.
- GPS Tracking and Navigation: The internet provides access to GPS technology and mapping services like Google Maps, enabling users to navigate efficiently, find directions, and avoid traffic congestion, enhancing travel experiences.
Disadvantages of the Internet
- Time Wastage: Excessive use of social media and aimless browsing on the internet can lead to a significant waste of time, reducing overall productivity. Instead of scrolling through social media feeds, individuals could utilize their time more effectively by engaging in skill-building activities or pursuing productive tasks.
- Negative Impact on Health: Prolonged internet usage can have adverse effects on physical health, as it often involves extended periods of sedentary behavior and screen exposure. More screen time can push the eyes and contribute to issues such as digital eye strain and headaches.
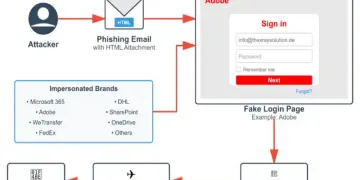
- Cyber Crimes: The internet is a breeding ground for various cybercrimes, including cyberbullying, spamming, viruses, hacking, and data theft. Cybercriminals can easily target individuals and organizations, compromising sensitive data and privacy.
- Effects on Children: Excessive exposure to the internet, including watching movies and playing games, can negatively impact the development of children. It may hinder their social interaction skills, physical activity levels, and overall personality development.
- Bullying and Spread of Negativity: Social media platforms have become avenues for individuals to spread negativity and engage in cyberbullying. Harmful and offensive messages can be easily circulated, leading to cyberbullying incidents and fostering a toxic online environment.
Society and the Internet
Society and the Internet have undergone a remarkable transformation since its inception. Initially a realm dominated by technical experts, the Internet swiftly evolved into a vital aspect of modern life.
By 2005, its penetration into American households rivaled the pace of electricity wiring, demonstrating its rapid integration into society. With 68 percent of American adults and 90 percent of teenagers utilizing the Internet, its influence extended globally, with Europe and Asia boasting similar connectivity rates.
However, there were disparities among nations; while countries like Taiwan and Japan led in online penetration, others such as India and Vietnam lagged behind.
Beyond mere statistics, the impact of the Internet on society is profound and multifaceted. It has transcended its role as a mere tool, becoming an integral part of daily existence.
Today, the Internet offers not only practical utilities but also the potential to shape virtual environments where individuals work, socialize, and even construct entire virtual realities. This transformation underscores the Internet’s evolution from a technical innovation to a lived experience that permeates every aspect of modern life.
Wrapping Up!
The internet has become an vital part of our daily lives. From its humble beginnings as a military experiment to the vast global network that it is today, the internet has revolutionized the way we communicate, access information, and conduct business.
Its endless possibilities and limitless potential have brought about countless opportunities for individuals and businesses alike.
The working of the internet may seem complex, but its basic functioning remains simple – sending and receiving data through interconnected computer networks. This has opened up a whole new world of communication and connectivity, allowing people to connect with each other from all corners of the globe.
Key Highlights What is Internet
- The Internet’s origins trace back to ARPANET, developed by the U.S. government in 1969 for military communication purposes.
- Initially conceived to withstand disruptions like military strikes, ARPANET evolved into a global network connecting computers worldwide.
- The Internet serves various purposes, including online banking and transactions, enabling money transfers and financial management.
- The Internet offers convenience and accessibility, allowing users to access services like banking and shopping from anywhere.
FAQ’s About What is Internet
1) How does the Internet work?
The Internet operates through interconnected computers and servers. Clients connect to the Internet via ISPs, accessing data stored on servers through web browsers and applications.
2) What are the primary uses of the Internet?
The Internet serves purposes such as online banking, education, entertainment, communication, and e-commerce. Users can perform tasks like money transfers, job searches, content consumption, social networking, and online shopping.
3) What are the disadvantages of the Internet?
- Time wastage and decreased productivity due to excessive use of social media and online platforms.
- Adverse effects on health, such as eye strain, sedentary behavior, and mental health issues.
- Cybercrimes, including hacking, phishing, and identity theft, pose risks to users’ privacy and security.
4) What are the advantages of using the Internet?
- Convenience and accessibility: Users can access services and information from anywhere.
- Educational and career opportunities: Extensive resources for learning, job searching, and freelancing.
- Entertainment options: Enjoyment of music, videos, games, and social media.