A new variant of Mirai botnet thriving on several vulnerabilities has been targeting Linux-based devices.
The three found vulnerabilities analyzed by researchers were CVE-2023-27076, CVE-2023-26801, and CVE-2023-26802.
The variant used in the Mirai botnet cyber attack, IZ1H9 exploited flaws in Tenda, LB-Link, and Digital China Networks. Several IoT devices were targeted by the Mirai variant IZ1H9, researchers of Unit 42, Palo Alto Networks stated in a report.
The incident that raised the alarm for the Mirai botnet cyber attack
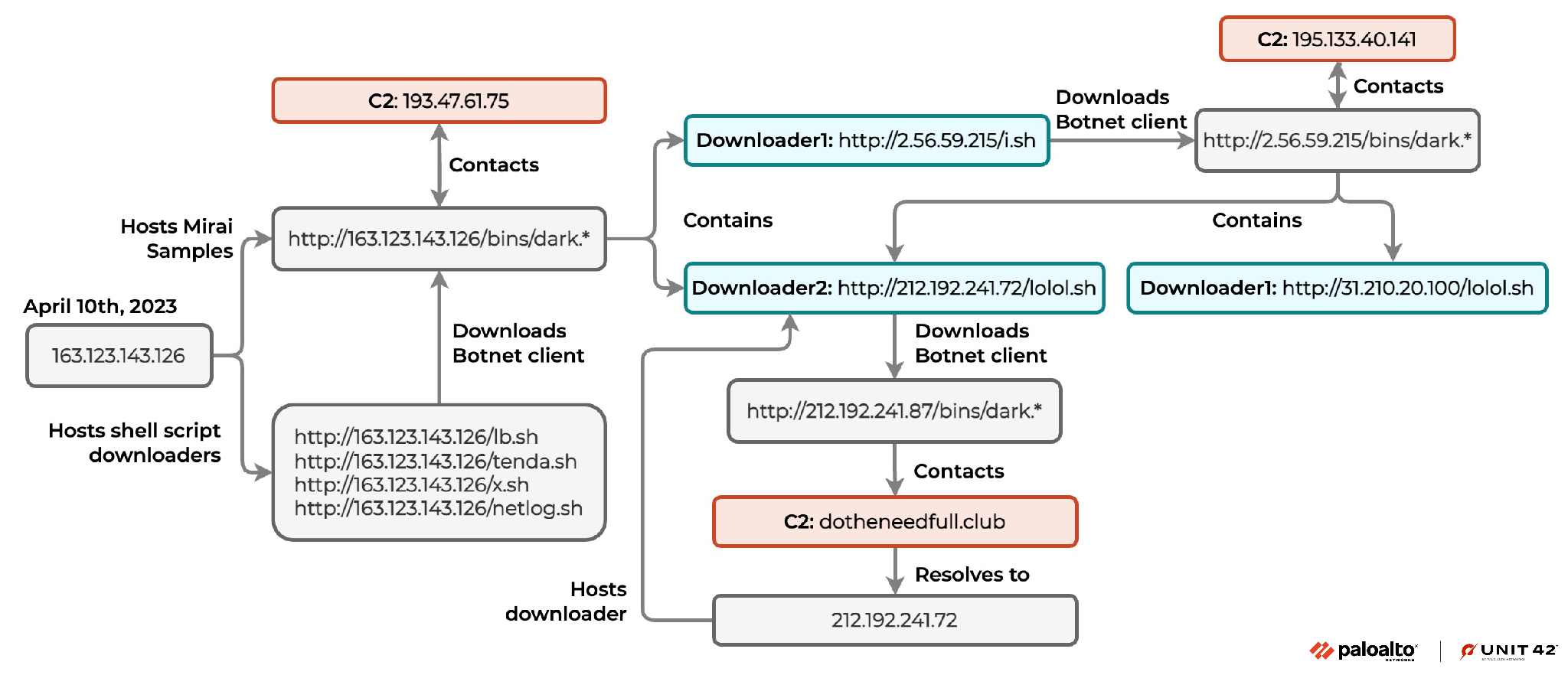
On April 1, 2023 Unit 42 researchers were alerted by the threat hunting system about abnormal traffic. They found that the hackers tried to download and execute a shell script downloader lb.sh from IP 163.123.143[.]126.
This Mirai botnet cyber attack was capable of deleting logs and hiding its tracks. It was programmed to download and execute other bot clients to launch attacks on various Linux architectures.
Some of the bot clients the Mirai botnet variant IZ1H9 would download are as follows:
- hxxp://163.123.143[.]126/bins/dark.x86
- hxxp://163.123.143[.]126/bins/dark.mips
- hxxp://163.123.143[.]126/bins/dark.mpsl
- hxxp://163.123.143[.]126/bins/dark.arm4
- hxxp://163.123.143[.]126/bins/dark.arm5
Results of successful Mirai botnet cyber attacks
Researchers noted that the last step in the Mirai botnet cyber attack was to block network connection from ports including SSH, telnet, and HTTP. The system would be left unable to connect the devices again remotely or recover from the cybercrime.
IZ1H9, a variant of the Mirai botnet
“Based on behavior and patterns Unit 42 researchers observed during the analysis of the downloaded samples, we believe that they are a variant of the Mirai botnet called IZ1H9,” the Unit 42 report read.
They further added that the IZ1H9 was discovered in August 2018 and it has been one of the most active Mirai variants.
The botnet client IZ1H9 would first look for infected IP addresses to launch attacks, and avoid targeting blocked IPs such as government networks, internet providers, and large technology companies.
Other findings of the Mirai botnet cyber attack
The downloaded botnet clients would connect with the command-and-control server which was found to be 195.133.40[.]141. The found URLs hosting shell scripts were –
- hxxp://31.210.20[.]100/lolol[.]sh
- hxxp://212.192.241[.]72/lolol[.]sh
“The shell script downloader from 212.192.241[.]72 would download botnet clients from hxxp://212.192.241[.]87/bins/, and those botnet client samples would contact the C2 domain dotheneedfull[.]club,” the Unit 42 report read.
Details about the vulnerabilities in the vendor products
- CVE-2023-27076 – This vulnerability in Tenda G103 v.1.0.0.5 was published on April 10, 2023. It had a base score of 9.8 making a critical flaw.
- CVE-2023-26801 – This vulnerability in LB-Link BL-AC1900_2.0 v1.0.1, LB-LINK BL-WR9000 v2.4.9, LB-LINK BL-X26 v1.2.5, and LB-LINK BL-LTE300 v1.0.8 was published about on March 26, 2023. It also had a base score of 9.8, a critical severity flaw.
- CVE-2023-26802 – This vulnerability in DCN (Digital China Networks) DCBI-Netlog-LAB V1.0 was published on March 26, 2023. It also had a severity score of 9.8.
Speaking about the command injection vulnerability CVE-2023-27076, the Unit 42 report read, “The command injection vulnerability is due to the failure to sanitize the value of the language parameter in the cgi-bin/luci interface of Tenda G103.”
CVE-2023-26801, also a command injection bug allowed hackers to target the LB-Link wireless router’s component – /goform/set_LimitClinet_cfg. Cybercriminals could execute arbitrary commands because the component would not sanitize the user input in the time1, time2, and mac parameters.
The vulnerability CVE-2023-26802 would fail to sanitize the user inputs, making way for remote code execution.
Impact of the Mirai botnet cyber attack
After gaining access and exploiting the vulnerabilities in the software, the Mirai botnet variant IZ1H9 could take full control of the device and perform any task programmed by the hackers.
Campaigns using the IZ1H9 variant of the Mirai botnet for cyber attacks were observed since November 2021.
Cybercriminals behind the Mirai botnet cyber attacks
Unit 42 researchers found reasons to believe that all the campaigns using the IZ1H9 variant of the Mirai botnet for cyber attacks are the same. T
his was because the malware shell script downloaders for campaigns were similar, and the Mirai botnet samples used the same XOR decryption key – 0xBAADF00D.
Moreover, the Mirai botnet cyber attack campaigns all used identical functions which was confirmed form the botnet samples. The infrastructure of the botnet client samples was also similar.
“For SSH and telnet channels, IZ1H9 inherits the most significant feature from the original Mirai source code: a data section with embedded default login credentials for scanner and brute-force purposes,” Unit 42 added to signify the reasons connecting the variant and Mirai.
It was found that Mirai and IZ1H9 both encrypted their login credentials with a 1-byte XOR key, further solidifying the claims that IZ1H9 was a variant of the Mirai botnet.