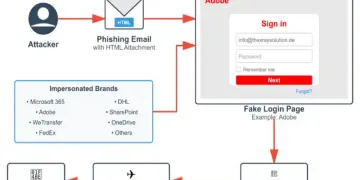
Phishing is a common hacking technique practised by cybercriminals to lure a target via a link or a message to conduct digital fraud. It is a type of social engineering wherein the message is explicitly designed for the desired target. Phishing works on pretence wherein the cyber-attacker pretends to be someone they are not. For instance, they may use well-known names to trick people into believing their bogus sale advertisements, free app links, job offer pdf, or anything the receiver may want access to.
Motives behind phishing scams
Phishing scams are frauds with different motives like stealing money, personal information, login data, banking information and other documents, sensitive information from a network of devices, etc. Depending upon what the scammers want, they may target individuals or organizations. The range of damage after falling prey to a phishing scam differs based on the intent of the phisher. They may use the stolen asset thus:
- To seek a ransom or money. They may either steal data and threaten to post the information online or use ransomware to make entire systems inaccessible to users.
- To seek bank details of a single or all the customers after hacking into its system to fraudulently withdraw their money, create fake credit cards, buy things using their banking credentials, etc.
- Spying on governments to find the information they need or may use to equip their future strategies. Like finding out about military preparedness to increase their strength comparatively.
- Defaming a company or a competitor by hacking into its systems and making public announcements about data breaches to cause doubt among its users and decrease its market value.
- Creating fear among people.
Common types of phishing attacks
There are several kinds of phishing attacks targeting individuals or larger groups and companies. The attacker pretends to be someone they are not to win the user’s trust and gain access to the information they seek. Some phishing techniques include:
- Spear phishing – Seeks sensitive data, usually by sending emails purporting to be someone credible, like a school, organization, or business.
- Vishing – Vishing or voice phishing involves making fake voice calls to have the target give away asked sensitive information.
- Email phishing – An attacker sends an email with bogus content that may have links that, when clicked, cause data loss by rendering remote access to the phisher.
- Pop-up phishing – Here, a pop-up window appears on the screen stating that the user must update their system antivirus using the options provided.
- Evil twin phishing – This technique uses a false Wi-Fi network that, when used by someone, gives access to phishers to their devices.
- Clone phishing – Just as the name suggests, the phisher clones or makes a duplicate message like the one the target usually gets from companies to win the user’s trust. The message may come with instructions, so they may do as per directed in it, ultimately leading to data theft. It could be done using emails or text messages.
- Water hole phishing – This attack usually targets a group. The phisher finds a website that the group usually visits and first infects it and then infects each target’s device.
- Deceptive phishing – A user is sent a fake message ‘alerting’ them about a phoney security issue facing their system. They are asked to take ‘preventive’ measures that instead infect their device.
- Whaling – Whaling is when a senior executive in a company is tricked into using a link to a website that looks official but is not. This helps the phisher gain access to every system the senior executive has access to steal high-level data.
- Social engineering – To extract money or data, social engineering attacks involves psychological manipulation pursuing individuals to click on links, share personal data, or both. The success rate depends on collecting information about the target after establishing a connection with them and executing the planned cyber-attack.
- Smishing – A phishing attack using an SMS is called smishing.
- Image phishing involves sending a laced or infected image using techniques like steganography to the target, which could steal user data or launch other attacks, including malware attacks.
- Search engine phishing – Here, search engine results like Google or Bing search show websites that are infected or fake as programmed by scammers. Users get duped into clicking on them and often entering their contact details during account creation or using an offered phoney product or service on the website.
- Website spoofing – Using a fake website that looks legitimate or resembles a well-known website, hackers cheat users into entering their credentials or using the spoofed website, causing data theft.
- Domain spoofing – Also called DNS spoofing, it involves using a fake website or email to appear like a domain of a known or any other legitimate company to dupe the user into entering their details on it.
The mechanism used by phishers
Phishers look for information that they can use to increase their access to more information they can bank upon. They use phone numbers, email addresses, social media accounts, etc., to send malicious messages. The message may require to be opened to be exposed to vulnerabilities or sometimes are self-executable. If the target senses that the communication seems doubtful and deletes it or does not click on the links therein, they may go unscathed by it. However, if they open the link, it may start malicious activities.
Often malicious links require additional steps like clicking, downloading, and installing a file. Unsuspecting targeted users go ahead and download malicious files because it has legitimate or reliable names on them. For instance, a student may be lured to click and download a pdf titled, ‘Most important exam questions.’ Social engineering works in a way wherein traps are created, keeping the target’s needs in mind.
Phishing can be done using a message with malicious word files, pdf, Excels, laced images, infected apps, etc. Some pop-ups and games have also been used for phishing which appears to be a legitimate message or advertisement but was indeed a phishing attempt.
How the scammers know their targets
The scammers may spy on targets or find bits of information from the dark web posted by another hacker. Depending upon what the cybercriminal seeks, they gain access to one target system and increase their reach to other connected devices to that same user through contacting each other. Such attack tactics have been seen in several companies, including the recent attack on the ride-sharing service provider Uber. After gaining access to an Uber employee’s company slack account, the scammer gained access to other connected accounts and systems and caused damage.
Impact of phishing scams
Phishing scams are known to bring down systems of enterprises as soon as the cyber-attacker gains access to them. They can ask for a heavy ransom to make quick money by hacking the systems, making the system inaccessible to the users, or asking for something in return for giving them access back.
When the attack does not go as planned
A ransomware attack that may have begun using a phishing link to gain access to the system may not always go as planned by the phisher. The user or organization may decline to pay a ransom. Regardless of the stance of the target, the cybercriminals may go ahead and cause damage such as:
- Selling or posting user data online or on the dark web.
- Increasing the damage by deleting data available in the hands of the hacker.
- Selecting users, using specific data from targeted companies, and sending them phishing links on their devices to steal their information or money.
- Causing more considerable damage impacting national security or critical infrastructures like railways or water lines to cause large-scale damage.
Avoiding phishing scams
- Appearance
Watch out for links, emails, text messages, and websites that only appear like their legitimate counterpart but are not entirely the same. This is one way to avoid falling prey to a phishing attack based on spoofing or creating fake lookalikes of websites, apps, or emails. Phishers may not always be wholly skilled or equipped to create their communication with the best quality software. So, if a user senses something amiss, it might be a phishing link.
- Typos
Often scammers usually do not go the extra mile in proofreading their content. This makes their messages have some or ample spelling and grammar mistakes. This is one way to detect that the phisher may not be skilled enough in the language or speaks another language. They may also use a translation tool to compose their content which would explain the errors.
- URLs
Some purported links to genuine websites or pages do not have the correct wordings in the URL. For example, a phishing email made to appear as if coming from their usual shopping app and claims to offer a gift prize upon clicking a dodgy link may not have the name of the company in the link. However, phishers may also create near-duplicate links as well. Detection can also be done depending on what they seek from the target. If what they offer does not seem legitimate, like an unexpected gift, free membership, free trip, heavy discount, etc., it could be a scam. A good way to cross-check if it is true is by opening another tab, checking the actual website, and seeking a reference to the said offer. The customer support team may also be able to help verify it. The user may also report the same to the legitimate company so they take the necessary steps to alert all other users and protect their systems.
- Seeking sensitive data
Phishing communications often use plots that sound like an urgent request, alerting of security issues or asking for bank details to offer something in return. Banks and all other companies have made it clear in most of their communications that they will never ask for bank credentials, log in details, or any such sensitive information online. It is only when a user calls the service provider or company to address an issue they are facing that they are asked for specific data to verify that they are the customer of that company.
- Anti-phishing add-ons
Using the device’s official app store, like the play store or browser tab, to download safe anti-phishing add-ons may help in minimizing pop-ups and other phishing campaigns reaching the device.
- Changing passwords and other details
Changing passwords or even swapping new ones with older ones if one has trouble remembering newer ones might help minimise falling prey to phishing attempts. This is especially important if the user has accidentally submitted their details to a suspicious entity. Similarly, if an app’s or bank account’s privacy is suspected to be compromised, passwords and credentials to those accounts must also be changed. Furthermore, banks or any specific service providers should be alerted with screenshots or copies of the phishing communications to have them secure the infected account from damage, including others’ accounts, as needed.
- Opting for multi-factor authenticators
Having multiple layers of authenticators while using an account or app helps deter unauthorized access. Because phishers may have access to login details by hacking, but they cannot always also have remote access to devices connected to the account to copy one-time passwords or access approval requests that are required in multi-factor authentication.
- Updating devices
Using up-to-date applications and software is very important to keep bugs away. Software developers of applications often immediately create security patches upon noticing a vulnerability or active exploitation of their service. Hence, updating and maintaining devices to their latest version is a very healthy practice.
- Using firewalls
External online attacks can be prevented using desktop firewalls and network firewalls. Similarly, using and updating antivirus software is also helpful in avoiding and detecting phishing attacks.
- Being aware of trends
Phishers may use the most trending news or topic to lure people. For instance, using the covid-19 pandemic to send phishing links in the name of treatments or news may be a ploy used by scammers. Similarly, they may keep an eye out for what users need and create phishing communication and links to launch their cyber-attack. Always crosschecking with genuine websites can help to not fall for such schemes.
Reporting phishing scams
As alert citizens and online users, it is the responsibility of each individual to alert local officials of phishing scams. The citizens of the United States of America can report phishing scams to the Federal Trade Commission (FTC).
- The phone lines are available at 18773824357 between 9 Am to 8 PM.
- Online reports to the FTC could be made using this link – reporting online scams.
- Emails about phishing scams could be made here – [email protected]
- A user can forward a phishing SMS they have received to the FTC. The FTC can be contacted by forwarding the text message to the number 7726.
- Alternatively, a user can use the official website to either report or find all the necessary information they need at https://reportfraud.ftc.gov/