After stabilizing in 2024, the growth of known exploited vulnerabilities accelerated in 2025.
That was one conclusion from Cyble’s analysis of CISA’s Known Exploited Vulnerability (KEV) catalog data from 2025. After growing at roughly 21% in 2023, with 187 vulnerabilities added to the CISA KEV catalog that year, growth slowed to about 17% in 2024, with 185 vulnerabilities added.
Growth in exploited vulnerabilities reaccelerated in 2025, with 245 vulnerabilities added to the KEV database, for a roughly 20% growth rate. The KEV catalog ended 2025 with 1,484 software and hardware flaws at high risk of attack.
The 245 flaws added in 2025 is also more than 30% above the trend of 185 to 187 vulnerabilities added the previous two years.
Cyble also examined vulnerabilities exploited by ransomware groups, the vendors and projects with the most KEV additions (and several that actually improved), and the most common exploited software weaknesses (CWEs).
Older Vulnerabilities Added to CISA KEV Also Grew
Older vulnerabilities added to the CISA KEV catalog also grew in 2025, Cyble said. After adding an average of 65 older vulnerabilities to the KEV catalog in 2023 and 2024, CISA added 94 vulnerabilities from 2024 and earlier to the catalog in 2025, an increase of nearly 45% from the 2023-2024 average.
The oldest vulnerability added to the KEV catalog last year was CVE-2007-0671, a Microsoft Office Excel Remote Code Execution vulnerability.
The oldest vulnerability in the catalog remains CVE-2002-0367, a privilege escalation vulnerability in the Windows NT and Windows 2000 smss.exe debugging subsystem that has been known to be used by ransomware groups, Cyble said.
CISA removed at least one vulnerability from the KEV catalog in 2025. CVE-2025-6264 is a Velociraptor Incorrect Default Permissions vulnerability that CISA determined had “insufficient evidence of exploitation,” Cyble noted.
Vulnerabilities Targeted in Ransomware Attacks
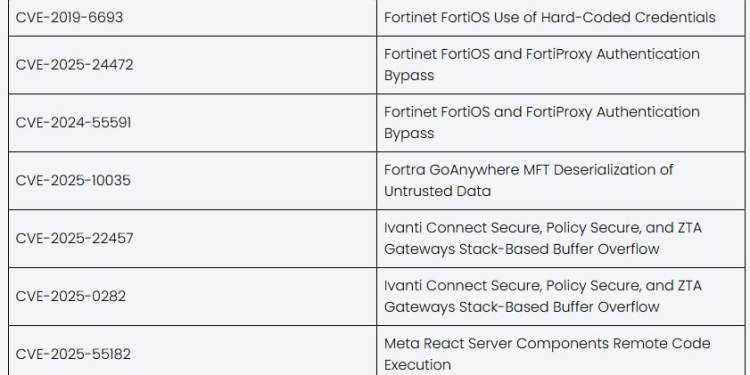
CISA marked 24 of the vulnerabilities added in 2025 as known to be exploited by ransomware groups, Cyble said. Those vulnerabilities include some well-known flaws such as CVE-2025-5777 (dubbed “CitrixBleed 2”) and Oracle E-Business Suite vulnerabilities targeted by the CL0P ransomware group.
Vendors with multiple vulnerabilities targeted by ransomware groups included Fortinet, Ivanti, Microsoft, Mitel, Oracle and SonicWall.
Projects and Vendors with the Most Exploited Vulnerabilities
Microsoft once again led all vendors and projects in CISA KEV additions in 2025, with 39 vulnerabilities added to the database, up from 36 in 2024.
Apple, Cisco, Google Chromium. Ivanti and Linux each had 7-9 vulnerabilities added to the KEV catalog.
Several vendors and projects actually improved in 2025, with fewer vulnerabilities added than they had in 2024, “suggesting improved security controls,” Cyble said. Adobe, Android, Apache, Ivanti, Palo Alto Networks, and VMware were among those that saw a decline in KEV vulnerabilities.
Most Common Software Weaknesses
Eight software and hardware weaknesses (common weakness enumerations, or CWEs) were “particularly prominent among the 2025 KEV additions,” Cyble said, noting that the list is similar to the 2024 list.
The most common CWEs in the 2025 CISA KEV additions were:
- CWE-78 – OS Command Injection – accounted for 18 of the 245 vulnerabilities.
- CWE-502 – Deserialization of Untrusted Data – was a factor in 14 of the vulnerabilities.
- CWE-22 – Path Traversal – appeared 13 times.
- CWE-416 – Use After Free – was a flaw in 11 of the vulnerabilities.
- CWE-787 – Out-of-bounds Write – accounted for 10 of the vulnerabilities.
- CWE-79 – Cross-site Scripting – appeared 7 times.
- CWE-94 (Code Injection) and CWE-287 (Improper Authentication) appeared 6 times each.