In the vast realm of the internet, where pop culture collides with hacktivism, crime, and terrorism, there exists a notorious online community that thrives on offensive content and serves as a breeding ground for criminal activities. This is the enigmatic story of 4Chan and its intriguing evolution into a hotbed for hackers.
Originally created as a response to Japan’s 2chan, 4Chan, which is also known as the “website with no rules”, started as a place for anime enthusiasts to discuss manga, comics, and their favorite TV shows.
However, as time passed, the website users began witnessing extremities and lawlessness on the platform, which caught the attention of the hacker community.
From leaked nude photos of celebrities to encouraging iPhone users to microwave their devices, 4Chan became a popular spot for everything wrong, including hacking.
Since its inception in 2003, the popular image board website has been involved in several controversies. However, things took a darker turn as users began witnessing anonymous confessions to murders, hacking sensitive data, and more on the website. Hacking remained a major concern because sensitive data was being leaked on the site, costing millions of dollars in damage, and reputation as well as gravely impacting the lives of people
Christopher Poole or also known by his online alias Moot, started 4Chan after being inspired by 2Chan, a Japanese imageboard that later inspired 4Chan — almost mimicking the original image board but catering to English-speaking communities.
One of the major successful traits of 4Chan was its ability to post anonymously and the inner engineer of the website allowing posts to disappear under a thread —- leaving no chance of evidence against criminals confessing their crimes online.

This route largely differs from the standard social media platforms where users are required to sign up with a name and email.
This unique feature was something that no other social media website was able to offer to its users — complete anonymity! The website’s founder was also baffled at the sheer number of visitors they were getting every month.
In a TED Talks show titled “The case for anonymity online,” Poole explained how 4Chan became one of the most visited websites in a couple of years.
With over 7 million monthly visitors, 700,000 posts per day, and 48 individual boards to use, the website was thriving in the early days of the internet and destroying every other social media platform in terms of daily traffic.
However, behind these jokes, memes, and funny cat videos, many popular threat actors and hacktivist groups began formulating on the platform.
Among those hacker groups, Anonymous, which was also a part of the 4Chan community back in the day, began experimenting with the 4Chan community with their channel “Marble Cake.
The group, which was yet to establish a name in the hacking community, gained international support from people demanding free speech with its campaign, “The Project Chanology.

During the TED Talk, Poole also spoke about the Tom Cruise controversy that triggered an extreme reaction on the platform, which eventually led to protests where several were hurt.
What was the Tom Cruise Church of Scientology controversy?
On January 14, 2008, a video by the Church of Scientology featuring an exclusive interview with Tom Cruise, was leaked on YouTube.
The video featured the Hollywood actor discussing his devotion to the “Church of Scientology” drew flak online as many termed Cruise’s behavior “strange”.
In response to the ongoing trolls and memes, the Church of Scientology took down the video from YouTube with a copyright claim. This angered the internet community and soon protests broke out.
“Scientology had this embarrassing video of Tom Cruise. It went online. They got it taken offline and managed to ‘piss off the internet’. So, over 7,000 people, in less than one month, organized in hundreds of cities around the globe and protested the Church of Scientology,” Poole explained during his TED Talk.
The protest went on for a couple of months, and many people got hurt. Poole also explained in the Ted Talks show that some individuals continued to protest against the Church of Scientology after two years of the incident.
The /b/ random board: Hacking for fun, nothing to lose!
The /b/ random board gave users the freedom to post literally anything on the platform. It was unlike any other boards on that platform, which were dedicated to users sharing information about their favorite games, anime, memes and more.
The /b/ random board was filled with posts threatening people for murders, asking users how to bury bodies, suicide-encouraging posts, and extremities that could get anyone arrested.
Moreover, it has been rumored that the world-renowned hacker group Anonymous also began their journey on the /b/ random board.
Anonymous started by doing silly pranks, such as prank calling companies, hacking small sites for fun, and sharing their data with the 4Chan community, but soon, these minor pranks turned into something big, and this hacker group soon became one of the most feared groups of individuals to ever exists on the internet.
On January 21, 2008, Anonymous shared its first official video titled “Message to Scientology,” claiming to “destroy” the Church of Scientology for brainwashing its members.
A couple of months after their warning, Anonymous hacked the website of the Church of Scientology and leaked their internal documents on the website. The hacker collective paved the way for hacktivists to be thought as more than just prank-calling teens.
However, hacking activities by 4Chan users continued to take an extreme form and went beyond free speech, activism, and protests.
In another incident, the 4Chan community hacked the third annual TIME 100 poll for World’s Most Influential Person. To achieve this feat, 4Chan members decided to make its founder Christopher Poole, the number 1 on the TIME 100 list, beating the likes of globally recognized figures such as Barack Obama, Vladimir Putin, and Oprah Winfrey.
The hackers on the imageboard forum created programs that were submitting millions of votes in favor of Poole. They even went as far as spamming multiple platforms with links dedicated to pushing the founder to the number one position.
However, that was just the beginning. In 2012, the same board members restarted the campaign, and this time, they made Kim Jong Un, the monarch of North Korea, the person of the year.
These incidents confirmed that /b/ random board members were not ordinary people but highly skilled individuals familiar with hacking and digital manipulations.
Bald For Bieber. Cutting For Bieber
By this point, it was evident that the /b/ random board was not afraid of anything as long as they got the last laugh. In this sense, they launched campaigns, hacking attempts, and defamatory polls.
But things turned dark when /b/ random board members began the “#baldforbieber” program, a one-of-a-kind prank that made people do unthinkable things to themselves.
In October 2012, the 4Chan community pushed a prank post about Justin Bieber having cancer, and their prank encouraged young girls to shave their heads in support of the pop singer.
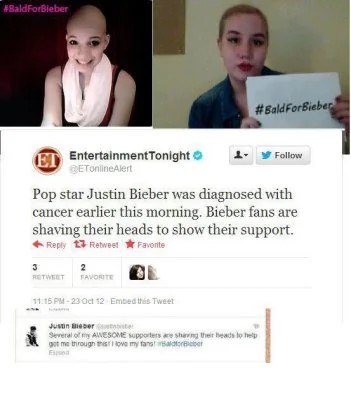
They also posted a fraudulent response from Justin Bieber for the campaign. The hashtag soon went viral prompting young girls into shaving their heads.
While Justin Bieber was nowhere associated with the campaign, in 2013, 4Chan’s/b/ random board pushed another campaign called “#cuttingforbieber.”
This campaign was targeting young girls and boys, encouraging them to cut themselves to make Justin Bieber stop smoking after TMZ leaked an image of the young pop star holding a blunt.
The /b/ random board continued running the fake campaign that was directly brainwashing young Justin Bieber fans to cut their wrists with razor blades, which prompted many to question on the authenticity of the internet.
The prank was initially started by a 4Chan user who posted this message on the /b/ random board, “Let’s start a cut yourself for Bieber campaign.
Tweet a bunch of pics of people cutting themselves and claim we did it because Bieber was smoking weed. See if we can get some little girls to cut themselves.”
4Chan cyberbullying: Destroying families and peace for a few giggles
For an outsider who has not invested much time on 4Chan, the community may seem like an innocent gathering platform for otakus, gamers, and pop culture enthusiasts, sharing their everyday life.
However, several stories suggest that the platform was a breeding ground for hacking and cyberbullying, targeting innocent users.
The infamous ‘Jessi Slaughter’ cyber horror was one among many such incidents, where the then 11-year-old girl became a target of 4chan trolls, leading to extreme cyberbullying and harassment.
Reports suggest that it all began when rumors of the YouTuber being sexually involved with Dahvie Vanity, the lead singer of the Blood on the Dance Floor band began circulating on social media platforms.
Jessi Slaughter responded to the rumor by posting a profanity-laden video on YouTube video mocking the “haters” stating that she did not care.
“If you can’t, like, realize that and stop hating, you know what? I’ll pop a Glock in your mouth and make a brain slushy”, she can be heard saying in the video, which soon went viral. Soon, the video began circulating with 4Chan users targeting Jessi Slaughter’ by leaking her real name, her father’s name, and even her address.
Things intensified after Jessi’s father appeared in one such video and threatened the online community with dire consequences for targeting his daughter.
The /b/ random board members began sending spam emails, fake police case calls, absurd items to her house. They also started flooding the email accounts of her parents.
Later, when Jessi appeared on Good Morning America (GMA), to discuss the cyberbullying incident, informing how the incident impacted her.
However, hackers on the platform continued to target individuals and even manipulated the 4Chan website to look like a family-friendly place for people. They exploited Google to show that the website was a cool place to hang out and that no profanity, bullying, or hacking occurred on its boards.
This operation was called the /b/ipolar, where the hackers were basically fooling the entirety of the internet into thinking that 4Chan was a family-friendly website.
Around the same time, Jessi went through different mental institutions, was denied internet access, and was put in foster care. Later, Jessi’s friend had also shared a video of Jessi apologizing to the public.
Jessi’s father died of a heart attack at the age of 53 and Jessi was reportedly diagnosed with fibromyalgia and was left wheelchair-bound.
It is evident that 4Chan is a problematic online community that poses significant risks to teenagers and young people. Throughout this report, we have explored why 4Chan is considered a bad place and why individuals must think rationally when engaging with such online communities.
The anonymous nature of 4Chan allows for the propagation of harmful and offensive content. Without accountability, users feel empowered to express extreme views, engage in cyberbullying, and spread hate speech. This toxic environment can harm the mental health and well- being of teenagers and young people, who are particularly vulnerable to online influences.
4Chan is also known for its involvement in illegal activities. The platform has been associated with the sharing and distribution of explicit and illicit content, including child pornography. Engaging with such content exposes young individuals to criminal behavior and perpetuates a cycle of exploitation and harm.
Given these factors, teenagers and young individuals must approach online communities like 4Chan cautiously and rationally. They should know the potential dangers and understand the implications of engaging in such platforms.
By critically evaluating the content they encounter and seeking reliable sources of information, young individuals can protect themselves from the negative influences on 4Chan.
In conclusion, 4Chan represents a toxic online community that poses numerous risks to the well-being and safety of teenagers and young people.
Individuals must reason, exercise caution, and prioritize their mental health when navigating the internet and engaging with online communities.
By promoting digital literacy, critical thinking, and responsible online behavior, we can mitigate the detrimental effects of platforms like 4Chan and foster a safer online environment for all.