The modern authentication ecosystem runs on a fragile assumption: that requests for one-time passwords are genuine. That assumption is now under sustained pressure. What began in the early 2020s as loosely shared scripts for irritating phone numbers has evolved into a coordinated ecosystem of SMS and OTP bombing tools engineered for scale, speed, and persistence.
Recent research from Cyble Research and Intelligence Labs (CRIL) examined approximately 20 of the most actively maintained repositories reveals a sharp technical evolution continuing through late 2025 and into 2026. These are no longer simple terminal-based scripts. They are cross-platform desktop applications, Telegram-integrated automation tools, and high-performance frameworks capable of orchestrating large-scale SMS and OTP bombing and voice-bombing campaigns across multiple regions.
Importantly, the findings reflect patterns observed within a defined research sample and should be interpreted as indicative trends rather than a complete census of the broader ecosystem. Even within that limited scope, the scale is striking.
From Isolated Scripts to Organized API Exploitation
SMS and OTP bombing campaigns operate by abusing legitimate authentication endpoints. Attackers repeatedly trigger password reset flows, registration verifications, or login challenges to flood a victim’s device with legitimate SMS messages or automated calls. The result is harassment, disruption, and in some cases, MFA fatigue.
Across the 20 repositories analyzed, approximately 843 vulnerable API endpoints were catalogued. These endpoints belonged to organizations spanning telecommunications, financial services, e-commerce, ride-hailing platforms, and government portals. Each shared a common weakness: inadequate rate limiting, insufficient CAPTCHA enforcement, or both.
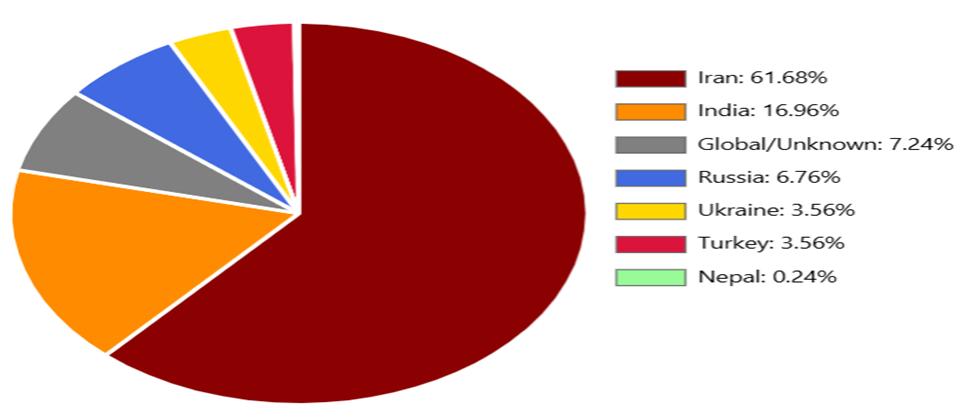
The regional targeting pattern was highly uneven. Roughly 61.68% of observed endpoints, about 520, were associated with infrastructure in Iran. India accounted for 16.96%, or approximately 143 endpoints. Additional activity focused on Turkey, Ukraine, and other parts of Eastern Europe and South Asia.
The abuse lifecycle typically begins with API discovery. Attackers manually test login and signup flows, scan common paths such as /api/send-otp or /auth/send-code, reverse-engineer mobile apps to extract hardcoded API references, or rely on community-maintained endpoint lists shared through public repositories and forums.
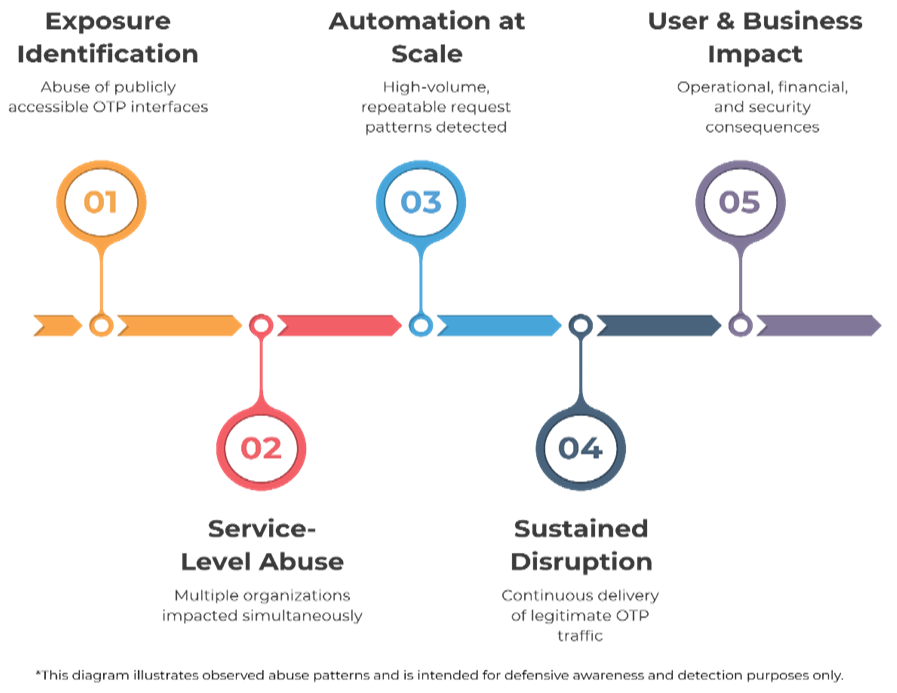
Once identified, these endpoints are integrated into multi-threaded attack tools capable of issuing simultaneous requests at scale.
The Rise of Automation and SSL Bypass Techniques
The technical stack behind SMS and OTP bombing tools has matured considerably.
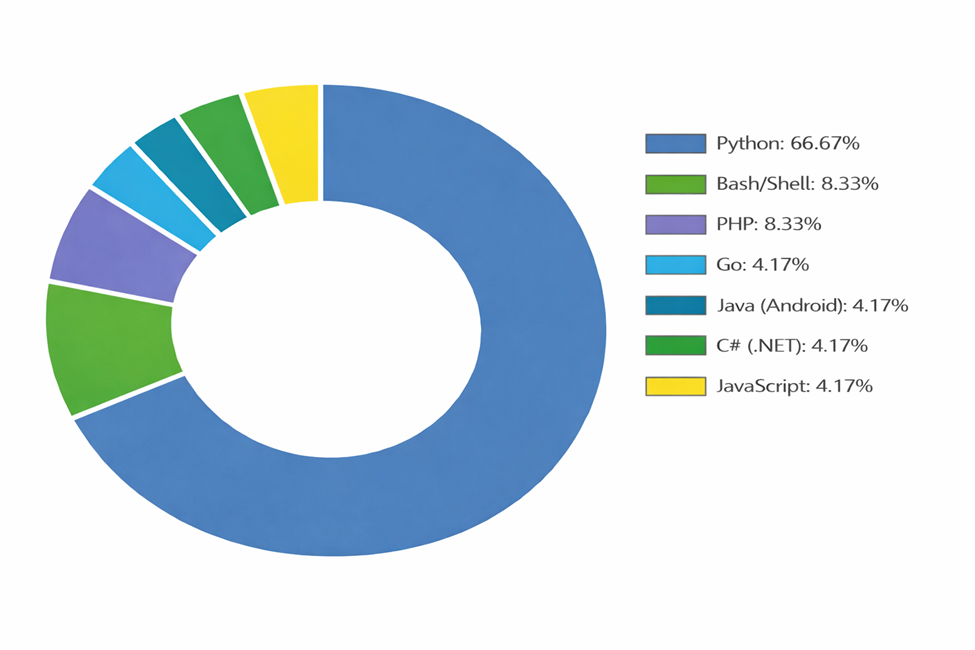
Maintainers now provide implementations across seven programming languages and frameworks, lowering the barrier to entry for attackers with minimal coding knowledge.
Modern tools incorporate:
- Multi-threading for parallel API abuse
- Proxy rotation to evade IP-based controls
- Request randomization to simulate human behavior
- Automated retries and failure handling
- Real-time reporting dashboards
More concerning is the widespread use of SSL bypass mechanisms. Approximately 75% of analyzed repositories disable SSL certificate validation to circumvent basic security controls. Instead of trusting properly validated SSL connections, these tools intentionally ignore certificate errors, allowing interception or manipulation of traffic without interruption. SSL bypass has become one of the most prevalent evasion techniques observed.
Additionally, 58.3% of repositories randomize User-Agent headers to evade signature-based detection. Around 33% exploit static or hardcoded reCAPTCHA tokens, defeating poorly implemented bot protections.
The ecosystem is no longer confined to SMS alone. Voice-bombing campaigns, automated calls triggered through telephony APIs, have been integrated into several tools, expanding the harassment vector beyond text messages.
Commercial Web Services and Data Harvesting
Parallel to open-source development, a commercial layer has emerged. Web-based SMS and OTP bombing platforms offer point-and-click interfaces accessible from any browser. Marketed deceptively as “prank tools” or “SMS testing services,” remove all technical barriers.
These services represent an escalation in accessibility. Unlike repository-based tools requiring local execution, web platforms abstract away configuration, proxy management, and API integration.
However, they operate on a dual-threat model. Phone numbers entered into these platforms are frequently harvested. Collected data may be reused for spam campaigns, sold as lead lists, or integrated into fraud operations. In effect, users expose both their targets and themselves to long-term exploitation.
Financial and Operational Impact
For individuals, SMS and OTP bombing can degrade device performance, bury legitimate communications, exhaust SMS storage limits, drain battery life, and create MFA fatigue that increases the risk of accidental approval of malicious login attempts. The addition of voice-bombing campaigns further intensifies disruption.
For organizations, the impact extends beyond inconvenience.
Financially, each OTP message costs between $0.05 and $0.20. A single attack generating 10,000 messages can cost $500 to $2,000. Unprotected API endpoints subjected to sustained abuse can push monthly SMS bills into five-figure territory.
Operationally, legitimate users may be unable to receive verification codes. Customer support teams become overwhelmed. Delivery delays affect all customers’ needs. In regulated sectors, failure to ensure secure and reliable authentication of flows may create compliance exposure.
Reputational damage compounds the issue. Public perception quickly associates spam-like behavior with poor security controls.




















































