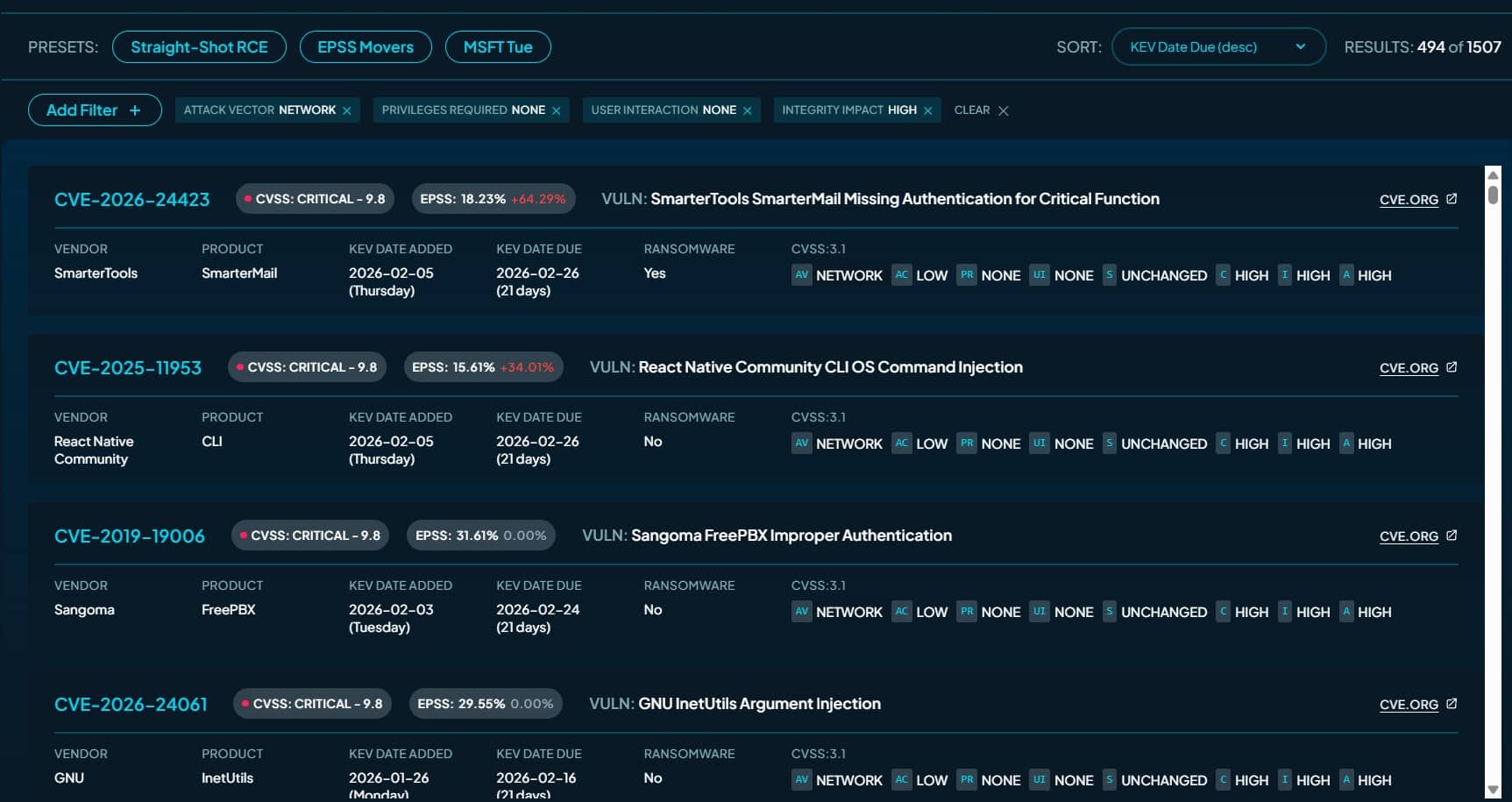
In today’s digital age, the dark web has emerged as a notorious underworld of the internet, accessible only through specialized software, where cybercriminals thrive, trading stolen credentials, intellectual property (IP), and financial information with alarming frequency. Dark web monitoring for CFO is not just a technical necessity but a crucial aspect of safeguarding an organization’s financial integrity and reputation.
For Chief Financial Officers, understanding and mitigating these risks is paramount to protecting their company’s assets and ensuring long-term stability. As stewards of their organization’s financial health, CFOs must recognize the significant threat posed by the dark web and implement strategies to stay one step ahead of potential breaches and fraud.
This article delves into the critical role of dark web monitoring for CFOs, exploring why it is essential and how it can be effectively integrated into broader risk management frameworks.
Critical Role of CFO in Cybersecurity: Balancing Risk and Protection
CFOs might not be cybersecurity experts, but their expertise in risk management makes them essential allies to the Chief Information Security Officer (CISO), who safeguards the organization’s data and systems. Dark Web Monitoring for CFOs becomes vital as CFOs need to ensure cybersecurity plans align with the company’s financial risk profile.
They must evaluate whether these plans adequately protect sensitive systems and data and empower employees to recognize and respond to fraudulent activities. Given the top risk management role, the CFO must confidently assess and accept the organization’s cyber risk level.
Cybersecurity is crucial for CFOs due to the significant financial impact of cyberattacks. For example, a 2023 study by IBM and the Ponemon Institute revealed that the average cost of a data breach was $4.45 million globally.
The 2023 Verizon Data Breach Investigations Report highlighted that nearly 95% of attacks are financially motivated, targeting confidential data such as customer credit card numbers, employee passwords, and direct financial assets through schemes like phony invoices and ransomware. With nearly half of senior executives predicting worsening attacks on accounting and finance and considering the reputational damage from breaches, the financial stakes are high.
Moreover, new regulations, like those from the U.S. Securities and Exchange Commission (SEC), demand public companies provide investors with detailed cybersecurity incident reports and periodic updates on cybersecurity programs. The SEC requires notification within four days if a cybersecurity incident is deemed “material.”
Additionally, compliance with laws like the Federal Information Security Management Act (FISMA) requires CFOs in government agencies to stay aware of security measures. All these factors underscore why CFOs must prioritize cybersecurity to protect their organizations’ financial health and regulatory compliance.
So, What is The CFO’s Role in Dark Web Monitoring
The CFO’s role in dark web monitoring is pivotal in ensuring that an organization’s financial assets and sensitive information are safeguarded against emerging cyber threats. Dark Web Monitoring for CFOs involves several key responsibilities:
- Strategic Oversight: The CFO must ensure that dark web monitoring services like Cyble Vision or Cyble Darkweb Intelligence are integrated into the company’s broader cybersecurity strategy. For instance, if a company’s financial data is discovered on the dark web, the CFO needs to be informed promptly to mitigate potential financial damage and address any breaches.
- Risk Assessment: CFOs must evaluate how well these monitoring services detect and address threats. This involves assessing the effectiveness of dark web monitoring tools in identifying stolen credentials or leaked financial information that could impact the organization.
- Financial Management: Allocating a budget for dark web monitoring is another crucial aspect. For example, if a company experiences a data breach due to a lack of monitoring, the financial implications could be severe, as evidenced by a 2023 study showing the average breach cost of $4.45 million. The CFO must ensure that investments in dark web monitoring are justified and aligned with the company’s risk profile.
- Collaboration with IT: The CFO should work closely with the Chief Information Security Officer (CISO) to understand the specific threats identified through dark web monitoring. For example, if the dark web monitoring service uncovers that company’s proprietary financial information is being traded, the CFO will need to coordinate with IT to enhance security measures and prevent further exposure.
Therefore, dark web monitoring for Chief Financial Officers is crucial for protecting financial data, managing risk, and ensuring that the organization’s cybersecurity strategy is both effective and financially sound.
Benefits of Dark Web Monitoring for CFO
Dark Web Monitoring for CFOs offers several key benefits that enhance financial and operational security. Here’s how it can be advantageous:
- Early Threat Detection: Dark Web Monitoring Services can identify stolen credentials or leaked financial data before it impact the organization. For example, if a company’s customer credit card information is found on the dark web, early detection allows the CFO to act swiftly to mitigate potential fraud and prevent significant financial losses.
- Enhanced Risk Management: By integrating Dark Web Monitoring for Chief Financial Officers, CFOs gain insights into potential risks related to financial and intellectual property theft. This proactive approach enables them to implement stronger safeguards and adjust their financial strategies accordingly, reducing overall risk exposure.
- Regulatory Compliance: Effective dark web monitoring supports compliance with regulations by ensuring that sensitive information is protected. For instance, if a financial services company discovers compromised data linked to a breach, timely dark web monitoring helps meet reporting requirements and avoid regulatory fines.
- Improved Decision-Making: Dark Web Monitoring for CFOs provides valuable intelligence that aids in making informed decisions about cybersecurity investments. For example, if monitoring reveals that a company’s proprietary financial data is being targeted, the CFO can justify increased investment in cybersecurity measures to protect against potential threats.
Dark Web Monitoring for CFOs helps safeguard against financial losses, supports regulatory compliance, and enhances decision-making processes by providing critical insights into potential threats.
What Are Dark Web Monitoring Services That CFO Can Use
Dark Web Monitoring for CFOs is crucial for mitigating cyber risks and safeguarding sensitive financial information. Several Dark Web Monitoring Services provide tools that can be particularly valuable.
Utilizing dark web monitoring services, like those provided by cybersecurity firms such as Cyble, enables CFOs to proactively manage and mitigate risks associated with financial data breaches. AI-Powered Cyber Threat Intelligence company Cyble offers a comprehensive dark web monitoring solution designed to help CFOs identify and respond to threats quickly. Key features include:
- Real-Time Alerts: Cyble provides immediate notifications if sensitive information, such as financial records or personal data, is detected on dark web forums.
- Threat Intelligence: The platform delivers in-depth analysis of emerging threats and compromised data, offering actionable insights into potential risks.
- Data Exposure Reports: Cyble generates detailed reports on data exposure, helping CFOs understand the scope and impact of a breach.
For instance, if a CFO uses Cyble’s services and discovers that their company’s financial data is being sold on dark web marketplaces, Cyble’s real-time alerts will notify them of the breach. This allows the CFO to coordinate with cybersecurity teams to implement immediate remediation measures, such as securing compromised accounts or enhancing security protocols.
To Wrap Up
As cyber threats become increasingly sophisticated, the need for vigilant monitoring and rapid response grows. By integrating dark web monitoring services into their overall risk management framework, CFOs can better safeguard their organization’s sensitive financial data and enhance their defense against potential breaches.
As we look ahead, the landscape of dark web monitoring will continue to evolve with advancements in artificial intelligence and machine learning. These technologies promise to enhance the accuracy and efficiency of threat detection and response.
Additionally, the growing complexity of cyber threats will likely drive further innovations in monitoring solutions, making it crucial for CFOs to stay informed about emerging trends and technologies.
Staying proactive and embracing these advancements will be key to maintaining a strong defense against the ever-changing threats of the dark web.
CFOs should prioritize dark web monitoring as a crucial element of their risk management strategy. Services like Cyble offer real-time alerts and comprehensive threat intelligence, helping you stay ahead of potential breaches and protect your organization’s financial assets effectively. Consider integrating Cyble’s solutions strengthening your cybersecurity defenses.
Discover more by scheduling a demo today!