The day began with the promise of a joyous celebration during the Jewish holiday of Sukkot, with the early morning sun casting a hopeful glow. But soon, it all turned dark as Daniel Levi, an attendee at the Supernova music festival in southern Israel, and many like her, attempted to escape after Hamas paragliders descended onto the scene, launching an attack that transformed the serene morning into a nightmare.
Dozens of terrorists seemed to emerge from thin air, advancing upon the crowd like malevolent apparitions, shooting from all directions. Festival attendees scattered around like ants, as the terrorists took one shot after another, sparing no one in sight.
Simultaneously, the Palestinian militant group launched a flurry of rockets at Israel and breached its defenses by air, sea, and land in a surprise attack.
“They began firing, and rockets filled the sky,” Levi recounted during an ABC News Live interview.
With nowhere to hide, Daniel and her friends decided to climb the trees instead of staying out in the open fields. They bore witness to the horrifying sight of people being shot down. Six agonizing hours passed while they clung to the branches, their hearts pounding in rhythm with the gunfire below.
As the daylight gave way to shadows, a glimmer of hope appeared. Daniel and her companions decided to make a daring escape, venturing into an open field and making their way toward a nearby stream.
The turning point came when they spotted a police vehicle approaching—a beacon of salvation in a landscape fraught with peril.
However, not all were as fortunate.
The massacre claimed the lives of hundreds, igniting the flames of the ongoing Hamas-Israel cyber war, a devastating conflict that has exacted a heavy toll on countless innocent lives.
Hamas-Israel Cyber War Goes Digital
The Hamas-Israel conflict has transcended the physical battlefield, spilling into the digital domain.
The rapid dissemination of deceptive claims and altered images was already a major concern, but the emergence of hacktivist groups aligning themselves with either side of the conflict has compounded these mounting apprehensions.
These self-proclaimed “digital warriors” make their presence known on popular social media platforms like X, formerly Twitter, and Telegram, where they boast of their cyber exploits, asserting successful attacks on critical organizations, although the evidence for their claims often remains elusive.
They go a step further by disclosing their intended targets and even sharing stolen sensitive information. This digital onslaught adds another layer of deception and complexity to the traditional battlefield, making discernment and truth-seeking crucial in these tumultuous times.
With the war’s physical and digital dimensions becoming intertwined, the motivations driving these cyber-attacks span a spectrum, encompassing objectives such as intelligence gathering, disruption of critical infrastructure, and the dissemination of ideological messages.
In essence, the primary objectives of these hacktivists are to intimidate and create chaos. Certain hacker collectives are also exploiting the conflict to advance their own objectives, employing it as a diversion to escalate their cyberattacks.
Prominent Hacktivist Groups Take a Stand
Hackers backing the war are unpredictable in their choice of targets, presenting challenges for security experts trying to anticipate their actions. While identifying which side hacker groups align with can give some insight into their motives, predicting their specific next target remains complex.
Shedding light on these cyber operations, Cyble, the leader in AI-based Threat Intelligence Solutions Provider, thoroughly analyzed a week into the Hamas-Israel conflict, noting the coordinated web of attacks and the fundamentalism fueling the conflict.
Since the start of 2023, the report noted, Israeli entities have faced DDoS attacks from hacktivists with political and ideological motives, although these attacks were relatively moderate in scale and reach.
Following heightened tensions along the Gaza Border, researchers at Cyble noted a surge in hacktivism on social media platforms, particularly using hashtags like #OpIsrael and #AlAqsaFlood, beginning on Saturday, October 7, 2023.

Moreover, hacktivist groups like Team insane PK, Garnesia Team, Garuda Security, Team Herox, Hacktivist Pakistan, Team Azrael, Mysterious Team Bangladesh, GB Anon 17, Executor Team Cyber, SYLHET GANG-SG, Lulz Security Agency and Ghosts of Palestine were quick to propagandize the campaign in favor of Palestine.
Dark Web, Social Media: A Breeding Ground for Cyberattack Claims
Several hacker groups have been boasting about their latest targets and victims on platforms like Telegram and X. Cybersecurity experts and threat intelligence platforms are constantly sharing these updates, highlighting the rapid escalation of this cyber war.
Among the initial attacks, hackers were noted targeting critical infrastructure and communication centers. Moreover, hackers with political motivations reportedly launched attacks on colleges, billboards, and newspapers within the initial weeks of the war.
On the dawn of Sunday, October 8, the Pro-Russia hacker group Killnet vocalized its plan to compromise all Israeli government systems using distributed denial-of-service (DDoS) attacks.
The hacker collective attributes the ongoing violence to Israel and alleges the nation’s support for Ukraine and NATO.
Post their declaration, Killnet claimed they momentarily disrupted an Israeli government portal and the Shin Bet security agency’s website, as reported by Time.
Anonymous Sudan, believed to be operating as a facade for Russian interests, expressed its backing for the “Palestinian resistance” and claimed responsibility for taking down the Jerusalem Post’s website. The incident was confirmed by the news organizations.
Two smart billboards near Tel Aviv were hacked, replacing the commercials with anti-Israeli content. The displayed content, as reported by CNBC, depicted the Israeli flag under fire and footage from Gaza.
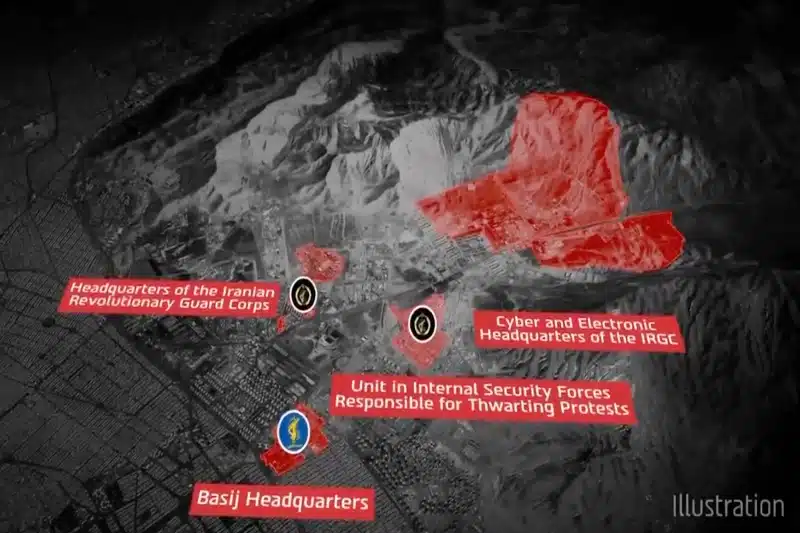
GHOSTS of Palestine was found to have exposed the IP addresses of Israel’s air defense system, the Iron Dome. A Telegram channel known as ‘AKSAR DDOS’ was also noted for discussions among its members regarding potential targets within the Iron Dome systems.


AnonGhost Official sought to sow panic by circulating fabricated nuclear threat warnings.
They claimed to have successfully breached the ‘Red Alert Israel’ national emergency phone application. Within this app, they generated numerous fake alerts, including deceptive notifications of a nuclear bomb threat.
Furthermore, the group shared a Proof of Concept (PoC) to exploit vulnerabilities in the Red Alert system, allowing them to compromise users’ mobile devices.

The hacktivist collective ‘Cyber Av3ngers’ has also gained prominence amid the Hamas-Israel war. Their tactics include launching DDoS attacks and achieving full system breaches.
As per insights from Cyble, this group has reportedly compromised several pivotal organizations in Israel, naming the Israel National Cyber Directorate, Bazan Group, Railway Authority, National Electricity Authority, Noga Enterprises, Dorad Energy Ltd., and Mekorot, recognized as Israel’s National Water Carrier.
Over 100 Active Hacker Groups Involved in the Israel and Palestine Conflict
The continuous conflict between Israel and Hamas brings forward nations’ challenges when addressing politically driven cyber groups. Hacktivists frequently target government-affiliated entities to disrupt wartime operations.
In another analysis of the Israel-Palestine cyberwar, threat intelligence platform FalconFeeds identified a total of 116 active hacker groups involved. Among these groups, 23 express pro-Israel sentiments, while a significant majority of 90 show support for the Palestinian side.
Interestingly, three groups have chosen to remain neutral and refrained from taking a stance in the conflict.
Breaking these groups down by their inclinations, a pronounced number of religious hacktivists from Asia and the Middle East have backed Palestine.
In addition, the pro-Russia hacker coalition KillNet, in alliance with Anonymous Sudan, has vocalized its support for Palestine. This alignment has stirred discussions, suggesting that some hacker groups may leverage the conflict to further their agendas.
Conversely, the report highlighted groups, predominantly from the Indian subcontinent like SilentOne and Indian Cyber Force, siding with Israel and significantly impacting the cyber warfare landscape.
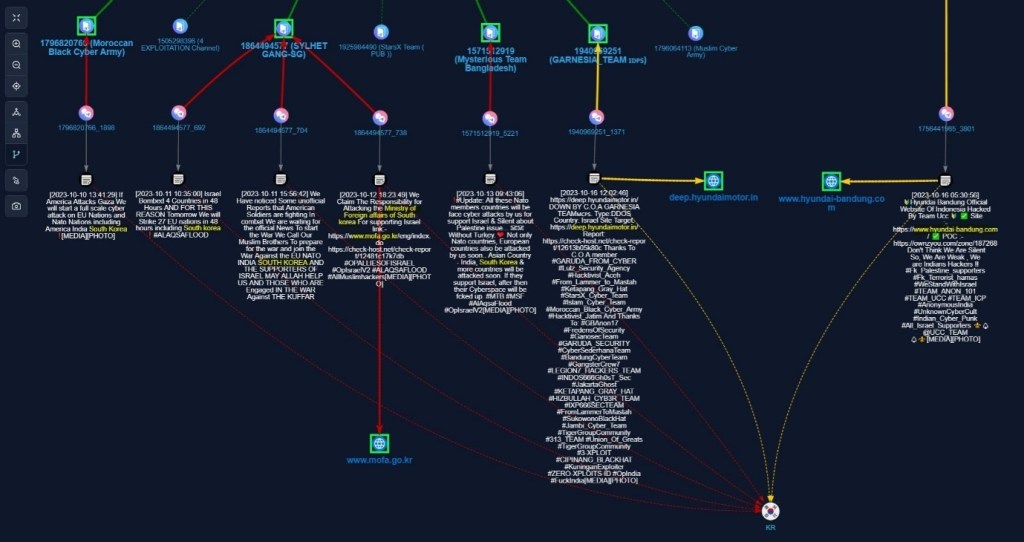
In a separate analysis conducted by Fusion Intelligence Center @StealthMole, a range of hacker groups expressing support for both Israel and Palestine were observed.
This analysis uncovered direct and indirect connections to hacker groups that have claimed or been alleged to have launched cyberattacks against South Korea. Adding to the absurdity of the affiliations and strategic positions among threat actors.
Moreover, it also emphasized the intricate and multifaceted nature of the cyber warfare within the Israel-Palestine conflict.
In the visual representation provided below, green lines are used to depict groups supporting Palestine, blue lines signify those advocating for Israel, red lines are employed to indicate references to direct attacks on South Korea, and yellow lines are utilized to highlight mentions of indirect attacks on South Korea.
The report highlights several prominent hacker groups that support Palestine. These groups include Ghostsec, Islamic Cyber Team Indonesian, Ghosts of Palestine, Cyber Error System, UserSec, We Are Killnet, Arab Anonymous Team, WeedSec, Ghost Clan, Team_Insane_Pakistan, TYG Team, Anonymous Sudan, Mysterious Team Bangladesh, Askar DDoS MY, Eagle Cyber Crew, and Cyb3r Drag0n.
Recent cyber incidents also illustrate a coordinated effort among pro-Iran and pro-Russia activist groups to support Hamas by complicating Israel’s response efforts. These cyberattacks have primarily involved basic tactics, like DDoS attacks and website defacements, which have minimal disruptive consequences.
Earlier in the month, Rob Joyce, the director of cybersecurity at the National Security Agency, mentioned at a Georgia-based security conference that, as of then, the U.S. Intelligence hadn’t witnessed substantial cyber campaigns in the Israel-Hamas fray.
However, he alluded to the potentiality of prominent cyber onslaughts in the offing. Joyce highlighted the possible emergence of more hacktivists and cautioned, “Sometimes, you don’t need to be sophisticated to have an impact.”
It is interesting to note that the number of hacker groups siding with Israel is extremely low as compared to those siding with Palestine, despite the unexpected large-scale assault being triggered by the attack by Hamas militants on Israel.
The question of which side – Palestine or Israel – receives more support is complex and varies depending on the context — politically, internationally, regional groups or public opinion. Hence, it is tricky to understand why more hacker groups are fighting for Palestine compared to Israel.
However, many experts have noted that several hacker collectives are often exaggerating their claims, attempting to seem more significant than they actually are.
Cybersecurity Capabilities: Palestine vs Israel
Sanjeev Relia, a cybersecurity expert, weighed in on the disparity between the hacker support for Palestine and Israel, referencing the cybersecurity prowess of both nations.
In strengthening Israel’s cyber capabilities, he accentuated the role of Unit 81, an elite technological division within the Israeli Military Intelligence Directorate.
“Unit 81 of Israel plays a significant role in advancing cyber technology. Many veterans from here, after their tenure, have launched cybersecurity startups, which have now grown into multi-billion-dollar businesses. With their deep understanding of security and cybersecurity, they significantly are helping Israel’s cyber defenses,” said Relia.
Highlighting the involvement of Unit 81 veterans in Israel’s cyber efforts, he remarked, “While they might not publicly acknowledge it, they are actively contributing to a significant portion of the offensive operations.”
Unit 81 is a secretive elite technological unit within the Israeli Military Intelligence Directorate. The unit is known for its advanced technological work on various projects, including cybersecurity, intelligence operations, and other technology-driven missions. Veterans of Unit 81 are individuals who have served in this unit and have since moved on from active duty.
On the flip side, discussing Hamas’s cyber capabilities, he inferred their exaggerated narratives on social media and their reliance on allied nations that aren’t particularly renowned for their cyber finesse.
Discussing Hamas’s cyber capabilities, he said, “They virtually have no capability, whatever capability is, is, from these nations who are supporting it, who themselves aren’t known for having advanced offensive cyber capabilities. Much of the narrative they have built on social media, including some shared images, has been exaggerated or manipulated.”
Another interesting aspect that surfaced following Hamas’s attack on Israel is the use of weapons originating from North Korea. During the attack on Israel, Hamas fighters appear to have used weapons originating from North Korea, as suggested by a militant video and weapons recovered by Israeli forces.
Recently, Hamas released photos showing their militants armed with a distinctively designed rocket-propelled grenade, which experts, including Matt Schroeder of the Small Arms Survey, identified as matching the features of Pyongyang’s F-7 weapon, as reported by AP.
While North Korea has historically been linked with supporting Palestinian militant groups, North Korean weaponry being found indicates direct support, which surely extends to the cyberwar as well.
North Korea’s cyber capabilities have significantly evolved over the past decade, and the nation has emerged as a notable player in cyber warfare.
Many of North Korea’s cyber operations have financial motivations. However, North Korea uses its cyber capabilities for espionage purposes as well.
The majority of North Korean cyber activities are believed to be state-sponsored. Some of the well-known groups associated with North Korea include Lazarus Group, APT38, and Hidden Cobra.
While several experts believe that the current Israel-Palestine cyber clash has become the most prominent display of cyber warfare since the Russia-Ukraine conflict, emphasizing the dramatic increase in hacker group participation in geopolitical disputes, this has also become a hotbed for misinformation and disinformation, with numerous claims being either fabricated or yet to be verified.
Digital Smoke and Mirrors: The Reality Behind Hacker Group Claims
The Cyber Av3ngers’ alleged cyberattack on Israel’s Dorad power plant marked one of the initial significant incidents during the onset of the Hamas-Israel conflict that garnered widespread attention. However, it was soon debunked.
Cyber Av3ngers took credit for this assault, flaunting PDF files and documents on their Telegram channel as evidence. They used imagery bearing the colors of the Palestinian flag along with snapshots of the purported attack to suggest their support for Palestine.
Despite these claims, Israeli authorities did not confirm the attack.
Subsequent media reports, complemented by an analysis from Kaspersky, revealed that the images circulated on Telegram were actually from a previous assault against multiple Israeli firms. This attack was orchestrated by the Moses Staff group in 2022. Notably, Moses Staff, believed to be an Iranian hacking collective, made its first appearance on hacker forums in 2021.
Alon Gal, the Co-Founder & CTO of Hudson Rock, called into question the authenticity of claims made by pro-Hamas hacker groups. These groups are alleged to have successfully infected Israeli computers with malware.
Gal’s findings, however, suggest that these purported “infections” on Israeli systems actually dated back to 2022 and were unrelated to the said pro-Hamas groups.
During a Flashpoint Israel-Hamas community call, Alon Gal spotlighted the ‘Haghjoyan’ hacking group. In a detailed LinkedIn post, he stated, “An example I recently came across… is the ‘Haghjoyan’ hacking group, which posted photos from Israeli computers on October 13th and provided a sample of some infected computers.”
Further investigation unveiled discrepancies. “Checking the sample in Hudson Rock’s database reveals that these computers are from 2022 and were not infected via any recent infection campaign,” Alon observed.
He wrapped up by noting, “It is common for these ‘pro-Hamas’ groups to either lie about cyberattacks or launch non-sophisticated attacks, emphasizing that such misleading claims often serve as an attempt by these groups to amplify their cyber capabilities or as tools for propaganda.
(Below are the false images claimed by the hacker group as posted on by Alon Gal)
An anonymous dark web researcher and analyst, when commenting on the cyberattack claims by hacker collectives and the nature of the attacks, stated, “Most of these attempts are superficial without sustained efforts or depth. They aren’t advanced persistent threats (APTs), just individuals expressing their viewpoints through hacking.
“There haven’t been any sophisticated attacks identified from the Palestinian side. They mainly utilize DDoS; such attacks are not advanced against infrastructure.”
He concluded by stating that only some of the claims were “authentic”, leading to pressing inquiries: Why are hacker groups perpetuating false claims amidst the conflict? What drives their intentions? What do they hope to accomplish by spreading misinformation? And does this foreshadow the emergence of more significant attacks in the near future?
The Imperative of Truth in the Age of Misinformation
As the frequency of cyberattack claims escalates, the number of verified incidents remains conspicuously low. Such a landscape makes it challenging to ascertain the veracity of hacktivist claims, potentially leading to the rampant spread of misinformation.
Regrettably, the damage has often been done by the time these allegations are debunked: lies tend to spread faster and wider than their subsequent corrections.
Behind every cyberattack claim, there may be more than just an attempt to spread false information. Such claims are, at times, strategic power moves.
Hacktivist groups may allege successful cyber breaches, intending to showcase their prowess and achieve a perceived victory—regardless of the truth behind such assertions.
Given the pattern of deceit that several hacktivist groups have shown in the past, one cannot take their claims at face value. However, these assertions, whether genuine or fabricated, can drain resources.
Intelligence and cybersecurity teams find themselves chasing down these claims, trying to verify their legitimacy. In scenarios where most claims end up being baseless, this process can divert crucial resources from more pressing security concerns.
However, the community isn’t remaining passive. A number of dedicated researchers are stepping up, rigorously investigating and debunking these assertions. By shedding light on the exaggerations and fabrications of certain groups, they’re aiming to mitigate the potential harm caused by such misinformation in the cybersecurity realm.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.