Unknown hackers exploited vulnerabilities in Ivanti software to infiltrate the Cybersecurity and Infrastructure Security Agency (CISA), leading to a significant breach of its networks. This CISA cyberattack forced the agency to shut down key systems in response to the breach.
As the primary guardian of infrastructure and cybersecurity for the entire US government, CISA’s targeting underscores the sophistication of the attack.
Approximately a month ago, CISA detected concerning activity indicating that its vital software, Ivanti products, were being leveraged for exploitation.
CISA Cyberattack Recovery
The Cyber Express reached out to CISA to learn more about this cyberattack and the steps taken by the security organization. In their response, CISA confirmed that they shut down two systems as a response to the ongoing vulnerability.
“About a month ago CISA identified activity indicating the exploitation of vulnerabilities in Ivanti products the agency uses. The impact was limited to two systems, which we immediately took offline. We continue to upgrade and modernize our systems, and there is no operational impact at this time”, said a CISO spokesperson in a conversation with TCE.
Furthermore, the response also denoted mitigation strategies against the Ivanti vulnerability and the steps users can take to minimize the attack. :We strongly urge all organizations to review our latest Ivanti advisory and take the steps outlined in it to protect their systems. While we do not have evidence, at this time, that any data was exfiltrated, our investigation is ongoing”, concluded the CISA spokesperson.
Prior to this incident, CISA had issued a warning in late February regarding cyber threat actors exploiting known vulnerabilities within Ivanti Connect Secure and Ivanti Policy Secure gateways. These products, integral to secure network access, had become targets for malicious actors seeking unauthorized access.
CISA Hacked with Broader Implications
The breach within CISA’s infrastructure became apparent when two critical systems were compromised. One of the affected systems was the Infrastructure Protection (IP) Gateway, housing crucial information concerning the interdependency of U.S. infrastructure.
‘The other compromised system was the Chemical Security Assessment Tool (CSAT), responsible for managing private-sector chemical security plans.
The exploitation of vulnerabilities within Ivanti products was not limited to CISA alone. The threat had broader implications, prompting federal and international cyber authorities to issue a global alert in late February.
It was advised that organizations using Ivanti products should take immediate steps to secure their systems, emphasizing the importance of having robust incident response plans in place.
The Ivanti Vulnerability
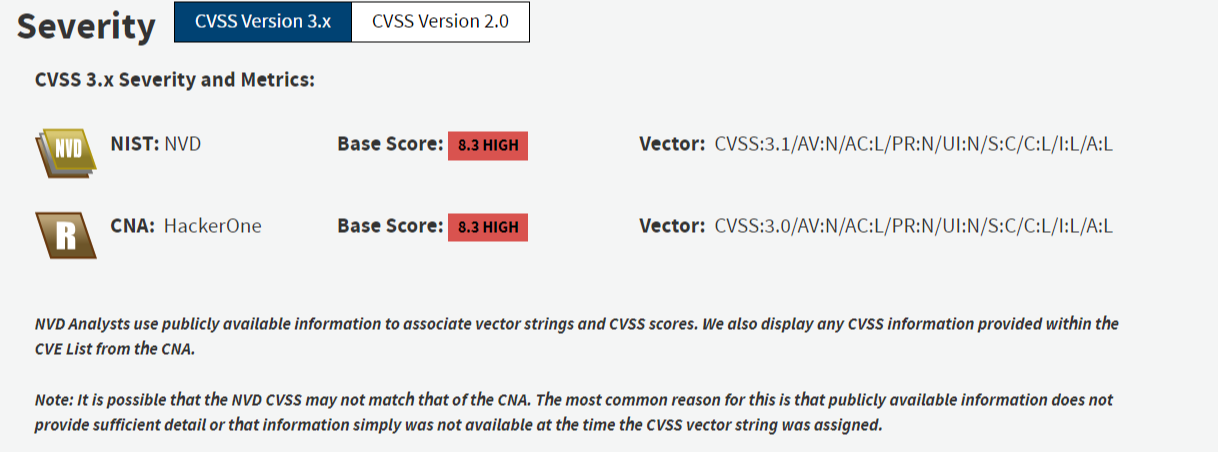
The Ivanti vulnerability or CVE-2024-22024 (XXE), affected Ivanti Connect Secure and Ivanti Policy Secure products and was part of the link connected to the CISA cyberattack. According to the National Cyber Security Centre (NCSC), the Ivanti vulnerability “is an authentication bypass vulnerability in the web component of ICS (9.x, 22.x) and IPS which allows a remote attacker to access restricted resources by bypassing control checks.”
Discovered during internal code review and disclosed by watchTowr, this vulnerability impacted specific versions of Ivanti Connect Secure (9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2, 22.5R1.1, and 22.5R2.2), Ivanti Policy Secure (22.5R1.1), and ZTA (22.6R1.3).
Patch updates were made available for affected versions. The provided mitigation was effective, and those who applied the patch released in January or February did not need to reset their appliances.
However, the security patches were released after weeks of exploitation activity, spilling the vulnerability assessment and its broader implications.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.