Filing a complaint with The U.S. Securities and Exchange Commission (SEC) in the event of a company’s non-disclosure of a cyberattack is primarily rooted in the principles of transparency, investor protection, and maintaining the integrity of the financial markets. However, what could it mean when a hacker group decides to meticulously fill out the SEC complaint form and post it on their leak site?
In a strikingly unconventional tactic, the infamous Alphv/BlackCat ransomware group filed a complaint with the U.S. Securities and Exchange Commission (SEC), accusing one of their claimed victims, MeridianLink, a California-based provider of digital lending and data verification solutions, of not adhering to a four-day rule for disclosing a cyberattack—a rule not yet in effect.
This move, a far cry from their usual modus operandi of covert operations and ransom demands, begs the question: What drives a hacker group to engage with a regulatory body traditionally allied with investors and market integrity?
At first glance, it may appear as an ironic twist – cybercriminals assuming the role of regulatory watchdogs. But a deeper analysis suggests a possible strategic ploy, a sign of desperation or an innovative tactic to amplify pressure for ransom.
This act, which witnessed a new form of exerting pressure and extortion by manipulating regulations designed for protection, compels us to examine the motivations and evolving strategies of cybercriminal groups in their relentless pursuit of illicit gains.
On November 7, 2023, BlackCat/APLHV claimed to breach the network of MeridianLink and extracted sensitive data. Following the MeridianLink data breach, the hacker collective demanded a ransom, setting a 24-hour deadline for payment to prevent the release of the stolen information.

Although initial communications were established, BlackCat/APLHV claims that MeridianLink has since failed to engage in further dialogue to negotiate the terms for the data’s security.
The company’s apparent silence on negotiation may have driven the hacker group to file a complaint with the SEC.
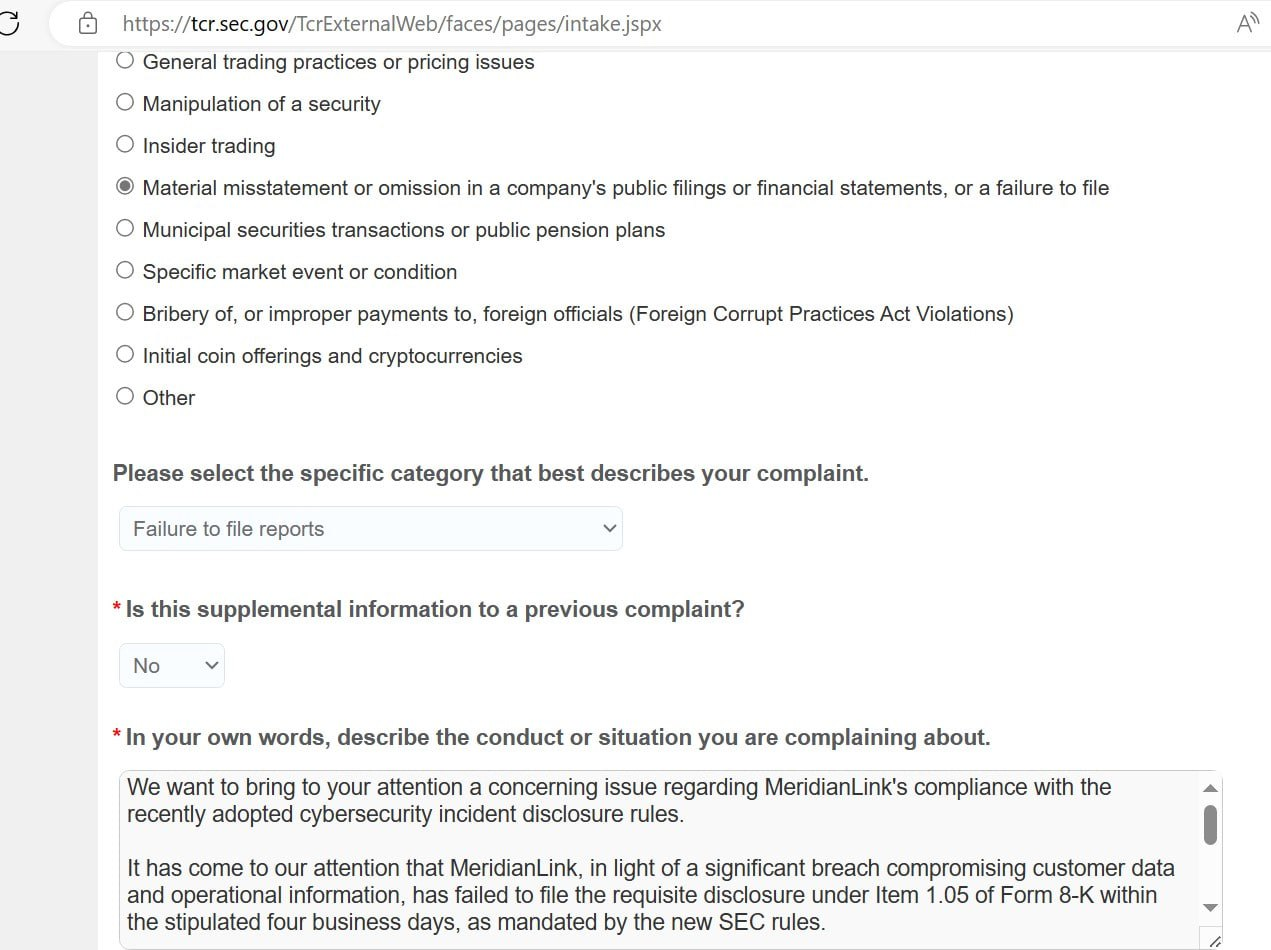
In the form they submitted, the hacker group highlighted, “We want to bring to your attention a concerning issue regarding MeridianLink’s compliance with the recently adopted cybersecurity incident disclosure rules.
“It has come to our attention that MeridianLink, in light of a significant breach compromising customer data and operational information, has failed to file the requisite disclosure under Item 1.05 of Form 8-K within the stipulated four business days, as mandated by the new SEC rules,” they wrote further.
The statement “failed to file the requisite disclosure under Item 1.05 of Form 8-K within the stipulated four business days, as mandated by the new SEC rules” refers to an accusation that a company, in this case, MeridianLink, did not comply with a specific reporting requirement set forth by the U.S. Securities and Exchange Commission (SEC).
Soon after, MeridianLink confirmed the cyberattack. A spokesperson from MeridianLink shared with The Cyber Express details about the cybersecurity incident, stating, “MeridianLink recently identified a cybersecurity incident.”
They continued, stating, “Based on our investigation to date, we have identified no evidence of unauthorized access to our production platforms, and the incident has caused minimal business interruption. If we determine that any consumer personal information was involved in this incident, we will provide notifications, as required by law.”
Form 8-K serves as a formal notification mechanism for informing shareholders of U.S. publicly traded companies and the Securities and Exchange Commission about certain events that could be significant to stakeholders or may require regulatory attention.
The SEC approved the final rules on cybersecurity, risk management, strategy, governance, and incident disclosure on July 26, 2023. These enhanced cybersecurity disclosure regulations officially came into effect on September 5, 2023, referred to as the “Final Rules.”
“With respect to compliance with the incident disclosure requirements in Item 1.05 of Form 8-K and in Form 6-K, all registrants other than smaller reporting companies must begin complying on December 18, 2023. As discussed above, smaller reporting companies are being given an additional 180 days from the non-smaller reporting company compliance date before they must begin complying with Item 1.05 of Form 8-K, on June 15, 2024,” stated the official report.
According to the report, starting December 18, 2023, all registrants—excluding smaller reporting companies—are obliged to follow the incident disclosure regulations.
This indicates that impacted companies have until December to comply with the newly established rules for reporting cybersecurity incidents. Several cybersecurity experts, who took to social media following the abrupt reaction by Alphv/BlackCat ransomware group, pointed this out.
“ALPHV claims the breach was November 7 MeridianLink says November 10. The amended SEC requirement says *material* incidents must be reported four business days after determining the incident is material. Compliance isn’t required until December 18th anyway,” tweeted Steve Werby, an information security strategist with 20 years of experience.
In conversation with The Cyber Express, Steve Werby shared his interpretation of the BlackCat hacker group’s stunt. He believes that the group’s decision to file a complaint with the SEC may not have been expected to change MeridianLink’s stance on the ransom but rather serves as a stark warning to future targets of the group, indicating that paying the ransom might be their sole escape from being publicly named and facing regulatory consequences.
Werby stated, “Since BlackCat’s threat of leaking the exfiltrated data didn’t result in a willingness to pay the requested ransom, it’s unlikely that they thought the SEC complaint would alter MeridianLink’s decision. It’s likely that the action was intended to signal to future BlackCat victims that ransom payment is the right choice. Perhaps with a dash of vengeance.”
Interestingly, the move to report “non-compliance” could backfire significantly.
A Cyber Threat Researcher from the cybersecurity and threat intelligence firm Cyble shared a perspective on the BlackCat ransomware group’s recent SEC filing. The researcher emphasized that this act is actually a display of boldness and a form of blackmail.
The researcher elaborated, “It’s not desperation, but rather flaunting and blackmail. The gangs see themselves as somebody who calls all the shots, and the victims have to submit to their demands.”
Further, they highlighted a potential unintended consequence of this tactic. “By reporting to the SEC, they might inadvertently prompt the government to implement stricter regulations. This could make it harder to pay ransoms, essentially undermining the primary motivation of ransomware gangs – getting paid.”
“This move is likely to backfire on them. It’s a positive development for the victims, as increased regulation will make the operations of ransomware groups more challenging,” they concluded.
Another viewpoint suggests that the hackers’ actions represent an attempt to manipulate the SEC’s cybersecurity regulations to their advantage.
Jamil Farshchi, EVP and Chief Information Security Officer (CISO) at Equifax, interprets this move as an aggressive tactic following unsuccessful ransom negotiations. By leveraging the SEC’s rules, which require companies to disclose significant cyber incidents, the hackers aim to exert additional pressure on their targets.
Farshchi explained, “It’s almost certainly a retaliatory response after not receiving a ransom.”
This statement indicates that the filing with the SEC could be a direct consequence of the ransomware group’s frustration over unmet demands.
He further added, “They are trying to weaponize the SEC cyber rules to incentivize future victims to pay the ransom.”
This tactic involves exploiting the regulatory requirements as a tool of coercion, pushing companies to pay ransoms to avoid the ramifications of public disclosure and potential regulatory scrutiny. Such a strategy could significantly impact companies, forcing them to weigh the risks of non-compliance with SEC rules against the consequences of yielding to the hackers’ demands.
BlackCat’s decision to file a complaint and publicly put it out also seems like a calculated strategy to instil fear among senior executives of companies, as pointed out by Greg Linares, a cybersecurity expert and white hat hacker.
“I definitely see it as a leverage tactic to induce fear among C-levels,” Linares told The Cyber Express.
He suggests that this tactic might have been chosen based on a vulnerability identified during the negotiation process with the victim company.
Expanding on the impact of this move, he added, “We don’t know why they potentially did this tactic, maybe it was based on a weakness discovered during negotiations, however I do know CISOs definitely took notice.”
Linares noted the significant attention the incident garnered on social media, predicting its potential influence on similar groups. “And with as much attention it received on social media, it likely will be replicated by other ransomware groups elsewhere in the near future.”
Discussing the implications for corporate cybersecurity strategies, Linares advised, “I think everyone should review their material reporting process, ransomware response, and tabletop exercises involving this plus other additional avenues of extortion.”
A dark web researcher at Cyble offered further insights into BlackCat’s strategy, describing it as a high-pressure tactic. According to the researcher, this move isn’t just about coercion; it’s also a calculated play for legitimacy.
“This seems to be a desperate attempt to pressure the victim into compliance,” they said.
Further, the researcher speculated on the group’s expectations: “It appears they hoped that the mere mention of an SEC notification would cause panic and prompt a swift response and possibly a quick settlement from the victim.”
Deciphering BlackCat’s Motives
The BlackCat ransomware group’s decision to file a complaint with the SEC represents a significant departure from traditional ransomware tactics, as conventional methods may meet increasing resistance.
One possible interpretation of BlackCat’s actions is that companies are becoming more resilient and less willing to agree to ransom demands. This shift could be a result of enhanced cybersecurity measures, better awareness, or the realization that paying the ransom offers no guarantee against data exposure. Companies are increasingly aware of the unreliability of hackers.
The realization that paying the ransom doesn’t necessarily safeguard against data exposure or future attacks, has left many companies in a dilemma. Faced with this new resilience, ransomware groups like BlackCat might be exploring more desperate and innovative tactics to exert pressure and secure payment.
The move also reflects the complications introduced by tighter regulations in cybersecurity. The requirement for companies to disclose cyberattacks to regulatory bodies like the SEC adds a new layer to the ransomware game. BlackCat’s decision to exploit these regulations indicates their awareness of the legal and reputational pressures that can be used as leverage against their targets.
Despite the uncertainty of securing a ransom, BlackCat’s approach has undoubtedly achieved the desired attention. This publicity, while not directly lucrative, enhances their notoriety and may serve as a warning to future targets.
In conclusion, BlackCat’s unusual tactic of engaging with the SEC is a move that speaks volumes about the current state of cybercrime. It suggests possible desperation on the part of hackers facing stiffer corporate resistance and complex regulatory landscapes. It also reflects an understanding that the promise of ransom payment is becoming increasingly unreliable.




















































