SigningHub has denied the allegations of the cyberattack orchestrated by the IntelBroker hacker. The UK-based online document signing and digital signature creation service provider has shared a blog post, detailing the false claims made by the threat actor.
The organization stated that “this claim has been found to be 100% false”, and upon analysis of the file purported to be the source code of Ascertia SigningHub, the organization denoted that the file does not include any source code or executable related to SigningHub or any other Ascertia product.
The SigningHub data leak, initially posted on the nuovo BreachForums, shared insights into the operation of the organization. IntelBroker, a known entity in the hacker community, revealed the breach on May 8, 2024, shedding light on an incident that allegedly occurred in December 2023.
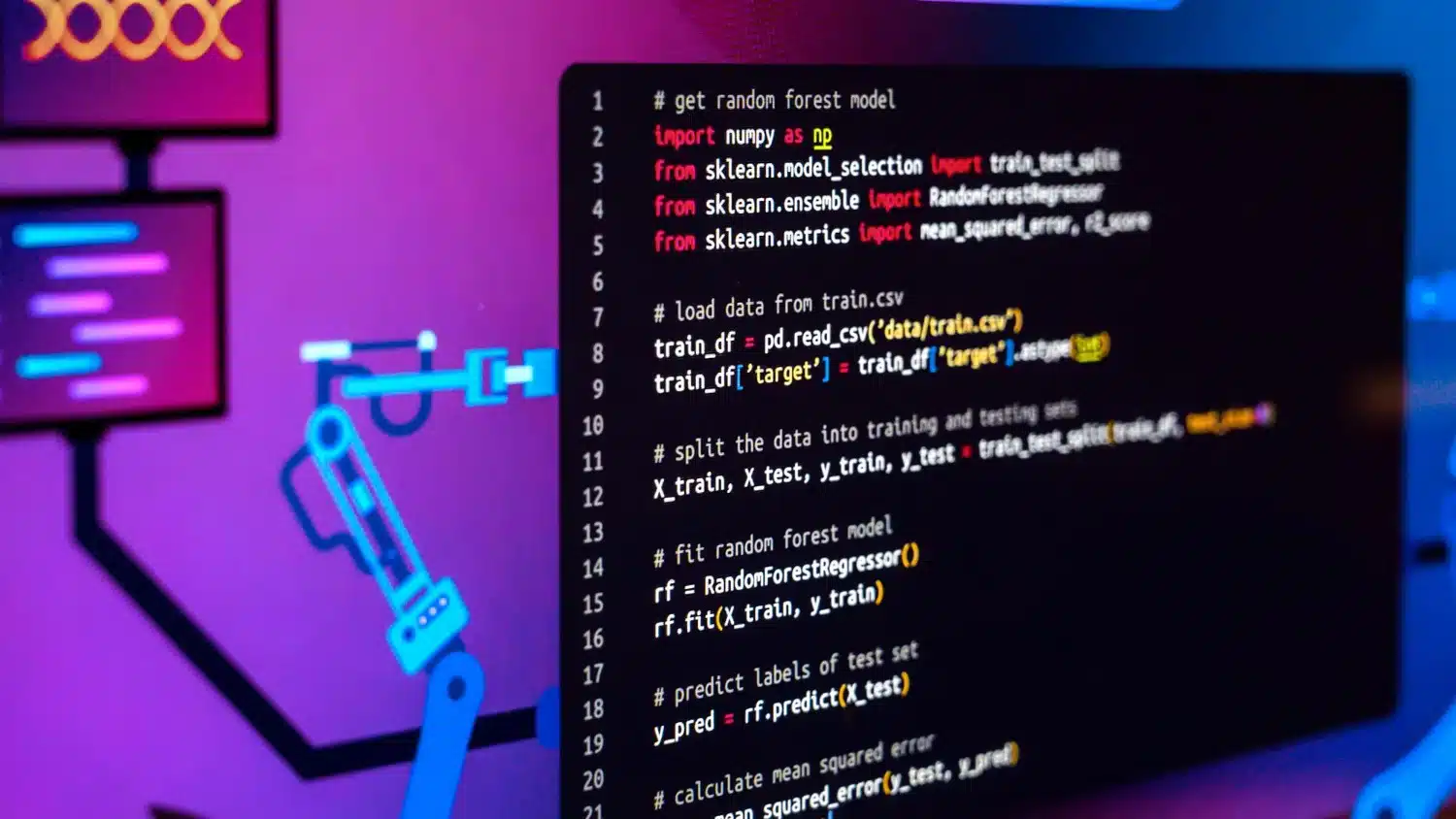
The leaked source code encompasses crucial elements of SigningHub’s infrastructure, including API services, docker container files, certificates, libraries, and other sensitive data.
Ascertia Denies Allegations of the SigningHub Data Leak
Following the SigningHub data leak claims, Ascertia responded to the claims via a blog post, stating the SigningHub data breach and source code leak to be false. Allegations arose on May 8th via Twitter/X, claiming unauthorized access to Ascertia’s network in December 2023.
After thorough investigation, Ascertia confirmed no breach or access to SigningHub’s source code. The file posted online purported to be SigningHub’s source code was analyzed, revealing no related content.
The Ascertia IT team simultaneously began a thorough investigation of the Ascertia network security systems and logs. At this time, Ascertia can confirm that there is no unauthorised access from bad actors and has concluded that the claims of a data breach are also false”, stated Ascertia.
Simultaneously, Ascertia’s IT team examined network security systems and logs, confirming no unauthorized access. Ascertia emphasizes its dedication to information security, GDPR compliance, and robust security measures. Ongoing analysis of network access points and systems ensures product, staff, and client data security.”
IntelBroker Claims SigningHub Data Leak

The announcement of the SigningHub data breach paints a grim picture of the intrusion and its alleged impact. The post, titled “SigningHub – File Signing SRC Leaked, Download!”, was shared by the threat actor while other users commended the hacker for this intrusion, stating the SigningHub code leak was “another great hit”, “top release” and other words of praise.
The Cyber Express has reached out to Ascertia to learn more about this SigningHub data leak. However, at the time of writing this, no official statement or response has been shared apart from the blog post by the parent company Ascertia.
In an attempt to shed light on the operation associated with the hacker, The Cyber Express reached out to IntelBroker for insights into their motivations and methods. In a recent interview, IntelBroker shared details of their hacking journey, affiliations, and previous exploits, highlighting the scale and sophistication of their operations.
The IntelBroker Modus Operandi and Recent Attacks
IntelBroker’s track record includes a series of high-profile breaches targeting organizations across various sectors, ranging from aviation and technology to government agencies.
Notable breaches attributed to IntelBroker include infiltrations at the Los Angeles International Airport, Acuity, General Electric, DC Health Link, and others, each revealing the extent of vulnerabilities in digital infrastructure.
The alleged breach at SigningHub adds another layer of complexity to the IntelBroker operations as the hacker has claimed multiple data breaches in 2024, highlighting the pressing issue of security.
The Cyber Express will be closely monitoring the situation and we’ll update this post once we have more information on the SigningHub source code leak or any official confirmation from the organization.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.