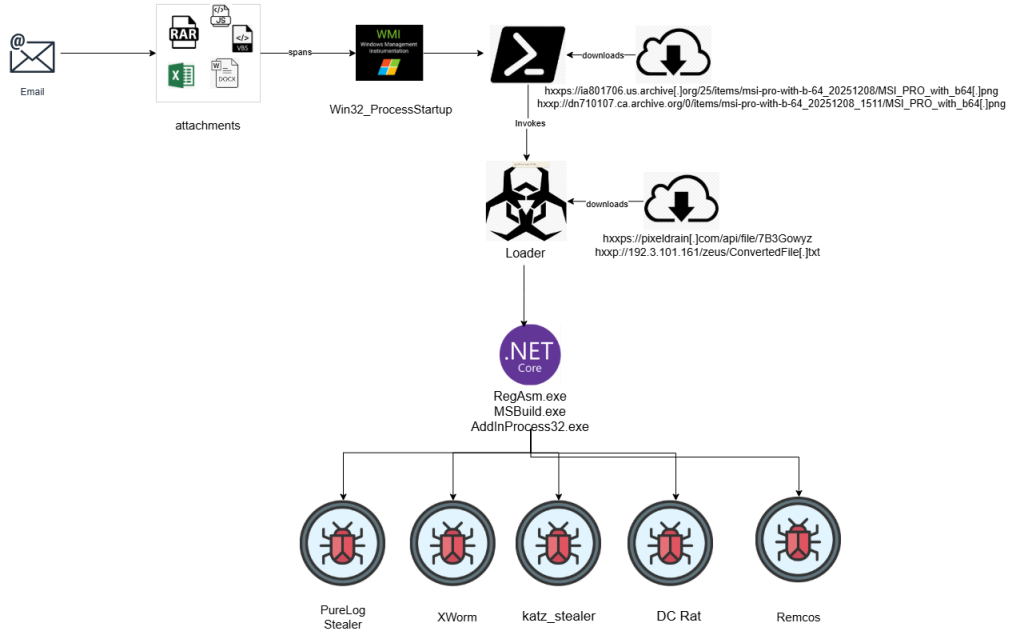
The recent update to CrowdStrike’s Falcon Sensor product precipitated a widespread issue, leading to mass blue screen of death (BSOD) errors on Windows computers worldwide. Falcon, described by CrowdStrike as a platform meticulously designed to prevent breaches through a comprehensive set of cloud-delivered technologies, experienced a significant malfunction that impacted millions of users, including major organizations and cloud platforms.
The outage was triggered by a defective update to CrowdStrike’s Falcon sensor, resulting in a logic error that caused system crashes, particularly on Windows devices. This disruption affected critical sectors, including banking, airlines, and healthcare, leading to interruptions in media and government operations.
In the aftermath, IT administrators were compelled to address the issue, often manually, while Microsoft released a tool to facilitate recovery. CrowdStrike has also deployed a fix and is providing ongoing updates and remediation steps to affected customers.
Despite these efforts, their stock has experienced a notable decline, and investor concerns are significant. So, what could CrowdStrike have done to prevent this incident? And what were some of the actions they executed well? This article outlines 10 critical lessons from the CrowdStrike outage.
Lessons From CrowdStrike Outage
Ensure Rigorous Pre-Deployment Testing
Rigorous pre-deployment testing is essential to identify and mitigate potential vulnerabilities before software is released into production. This testing phase involves comprehensive assessments, including unit tests, integration tests, system tests, and user acceptance tests.
The CrowdStrike outage highlights the necessity of thorough pre-deployment testing. The logic error in the Falcon sensor update, which led to widespread system crashes, could have been identified and rectified through more rigorous testing. Furthermore, rigorous testing protocols can simulate various scenarios, including edge cases and stress conditions, ensuring the software’s robustness under different circumstances.
Effective pre-deployment testing would have identified the faulty configuration update before it was deployed, thus avoiding the significant operational disruptions experienced by users. This comprehensive approach not only improves the software’s reliability but also enhances user trust and reduces the risk of costly post-deployment fixes and reputational damage.
Prioritize Incident Response Training
Incident response training is crucial in cybersecurity as it prepares organizations to effectively handle and mitigate the impact of security incidents. This training equips personnel with the necessary skills and knowledge to respond promptly and efficiently to a range of cyber threats, such as malware attacks, data breaches, and system outages.
This was a success on CrowdStrike Flacon’s part as quick identification and remediation of logic error reduced the extent to which the system was down and impacted, showing the importance of well-prepared incident response teams. Proper incident response training involves developing a comprehensive incident response plan, and drills, and staying updated with the latest threat intelligence.
These measures ensure that the teams can quickly detect, and deal with threats, reducing the potential damage to the organization. Additionally, incident response training fosters a culture of security awareness and preparedness, encouraging proactive measures to prevent incidents from occurring in the first place. It also includes communication protocols, ensuring that all stakeholders are informed and coordinated during an incident.
Foster International Cybersecurity Cooperation
International cooperation in cybersecurity is vital due to the global nature of cyber threats. Cyberattackers do not respect national borders, and a coordinated international response is essential to effectively combat these threats. This cooperation involves sharing threat intelligence, best practices, and incident response strategies among countries and organizations.
The global reach of the CrowdStrike outage affected systems worldwide. International cooperation and the sharing of information between them are vital to address such widespread issues swiftly and efficiently, helping organizations across different countries to enhance their collective cybersecurity posture, improve their ability to detect and respond to threats and reduce the risk of widespread damage from cyber incidents. International cooperation also facilitates the development of global cybersecurity standards and frameworks, promoting consistency and interoperability in security practices.
Additionally, joint efforts in research and development can lead to innovative solutions to emerging cyber threats, benefiting all participating nations. This collaborative approach also helps in building trust and strengthening diplomatic relations, as countries work together to address a common challenge. Overall, focusing on international cooperation in cybersecurity is crucial to creating a safer and more secure digital environment for everyone.
Conduct Regular Audits and Testing
Regular audits and testing are critical components of a robust cybersecurity strategy. Regular audits involve systematically reviewing and assessing an organization’s security policies, procedures, and controls to identify weaknesses and ensure compliance with industry standards and regulations. Testing, on the other hand, includes activities such as vulnerability assessments, penetration testing, and security scans to detect and address potential vulnerabilities before they can be exploited.
The CrowdStrike outage demonstrated the importance of regular audits and testing. The faulty update that caused system crashes could have been detected through more frequent and thorough testing protocols. By conducting regular audits and tests, organizations can identify and rectify security gaps, ensure the integrity of their systems, and maintain a high level of security.
These practices also help in continuously improving the security posture of an organization, making it more resilient to cyber threats. Furthermore, regular audits and testing foster a proactive approach to cybersecurity, enabling organizations to stay ahead of potential threats and minimize the risk of costly breaches and downtime.
Cybersecurity Expertise and Funding
As cyber threats become increasingly sophisticated, the importance of cybersecurity expertise and funding cannot be overstated. Skilled cybersecurity professionals are essential for developing, implementing, and managing effective security measures. Adequate funding is crucial to support these efforts, allowing organizations to invest in advanced security technologies, conduct regular training, and stay updated with the latest threat intelligence.
The CrowdStrike outage highlighted the need for high levels of expertise and resources to quickly identify and remediate the issue. The complexity of cybersecurity threats and the sophistication required to manage and mitigate them, along with increased investment in cybersecurity expertise and funding is essential to develop robust systems and prevent similar occurrences. With the growing frequency and complexity of cyberattacks, organizations must prioritize building and maintaining a strong cybersecurity workforce.
This includes not only hiring skilled professionals but also investing in their continuous education and training. Adequate funding ensures that these professionals have access to the necessary tools and technologies to protect the organization’s assets effectively. Additionally, a well-funded cybersecurity program enables organizations to implement comprehensive security measures, conduct regular audits and testing, and develop robust incident response plans.
Balance Efficiency with Security
Balancing efficiency and security are crucial in today’s fast-paced digital environment. While operational efficiency is important for business success, it should not come at the expense of security. While rapid deployment of updates is important, the CrowdStrike outage demonstrated that prioritizing speed over thorough security checks can lead to severe consequences.
Ensuring that security measures are not bypassed or overlooked in the pursuit of efficiency is essential to prevent vulnerabilities that could be exploited by cyber attackers. This involves implementing security protocols and controls that are integrated seamlessly into the organization’s processes, allowing for both efficiency and robust protection.
Organizations should foster a culture where security is seen as a fundamental aspect of operational processes, rather than a hindrance. By doing so, they can achieve a balance that enables them to operate efficiently while maintaining a high level of security. Additionally, regular reviews and updates to security policies and procedures can help ensure that they remain effective and do not impede business operations unnecessarily.
Maintain Transparent Communication During Incidents
Effective and quick communication is vital for tech companies, especially during a cybersecurity incident. Timely communication ensures that all stakeholders, including customers, employees, and partners, are informed about the situation and the steps being taken to resolve it.
The CrowdStrike outage highlighted the importance of quick and transparent communication, as timely updates and clear communication with customers helped mitigate the impact and guide them through remediation steps. Prompt communication can prevent the spread of misinformation, reduce panic, and maintain trust. It also enables coordinated efforts in mitigating the impact of the incident, as everyone is aware of their roles and responsibilities.
Tech companies should establish clear communication protocols and channels to ensure that information is disseminated quickly and accurately. This includes preparing templates and guidelines for different types of incidents, conducting regular communication drills, and maintaining an up-to-date contact list of all stakeholders. By prioritizing quick communication, tech companies can enhance their incident response capabilities, minimize the impact of security incidents, and protect their reputation.
Implement Phased Rollouts for Updates
Phased rollouts of updates are an effective strategy for managing the deployment of new software or system changes. By releasing updates in stages, organizations can monitor the impact of the changes on a smaller scale before a full-scale deployment. This approach allows for the early detection and resolution of issues, minimizing the risk of widespread disruption.
The CrowdStrike outage, which affected a large number of systems simultaneously, highlighted the potential benefits of phased rollouts. If the update had been deployed in phases, the logic error might have been identified and corrected before it impacted a significant number of systems.
Phased rollouts also enable organizations to gather feedback from a smaller group of users, allowing for further refinement and optimization of the update. This method not only reduces the risk of major issues but also enhances the overall quality and reliability of the software.
Adopting a multi-cloud strategy could also be helpful. This involves using multiple cloud service providers to distribute workloads and reduce the risk of downtime and data loss. This approach enhances redundancy and resilience, ensuring that if one provider experiences an outage, the organization can continue operations with another.
Ensure Business Continuity with Backup Servers and Alternative Data Centres
Backup servers and alternative data centers are critical components of a comprehensive IT strategy, especially for businesses that rely heavily on digital operations. They serve as a safeguard against data loss and system failures, ensuring business continuity and minimizing downtime. The CrowdStrike incident highlighted the need for robust disaster recovery plans to quickly restore affected services and reduce operational impact.
Backup servers are dedicated servers used to store copies of critical data and system configurations. Their primary function is to provide a recovery option in case the primary system encounters a failure or data corruption. Regular backups ensure that recent data can be restored quickly, reducing the risk of data loss from hardware failures, software malfunctions, or cyber-attacks. Backup servers can be configured to perform automation which optimizes storage use and speeds up recovery times.
Alternative data centers are facilities are secondary locations where a business can replicate its IT infrastructure and data. They provide an additional layer of protection by hosting copies of the primary data and applications in geographically separate locations. In the event of a disaster, such as a natural calamity or a significant technical failure, operations can switch to the alternative data center, ensuring that services remain operational, and data remains intact.
Automate Routine IT Processes to Minimize Human Error
Automation of routine IT tasks, such as backups, updates, and system monitoring, is essential for efficiency and reliability. Automation can help minimize human errors, such as those that might have contributed to the logic flaw in the CrowdStrike update. By automating routine IT processes, organizations can ensure more consistent and reliable system management.
Automated systems reduce the likelihood of human error, ensure consistency in processes, and free up IT staff to focus on more strategic tasks. For instance, automated backup solutions can schedule and perform regular backups without manual intervention, ensuring that backups are timely and comprehensive. Similarly, automation tools can manage updates and patch installations, keeping systems secure and up-to-date without the need for constant oversight.
Effective cybersecurity protocols and measures could have significantly mitigated the impact of the CrowdStrike outage. Regularly testing updates before widespread deployment would have likely identified the defective update early. Implementing the other recommended practices we discussed could have also prevented the situation we are facing now.
However, it’s important to acknowledge that not everything is negative. CrowdStrike’s incident response and quick communication were handled exceptionally well. We hope this event serves as a lesson for companies to prioritize cybersecurity, as even minor issues can have a significant snowball effect. By considering what CrowdStrike did well and what could have been improved, organizations can enhance their cybersecurity measures and prevent similar incidents in the future.