The Qilin ransomware group has been by far the most active ransomware group over the last seven months, so two new research reports detailing some of the group’s tactics, techniques and procedures (TTPs) are worth noting.
Trend Micro researchers examined a Qilin attack – the group is identified as “Agenda” by Trend – that deployed the group’s Linux ransomware variant on Windows systems, while Cisco Talos also looked at the group’s methods, including defensive evasion techniques.
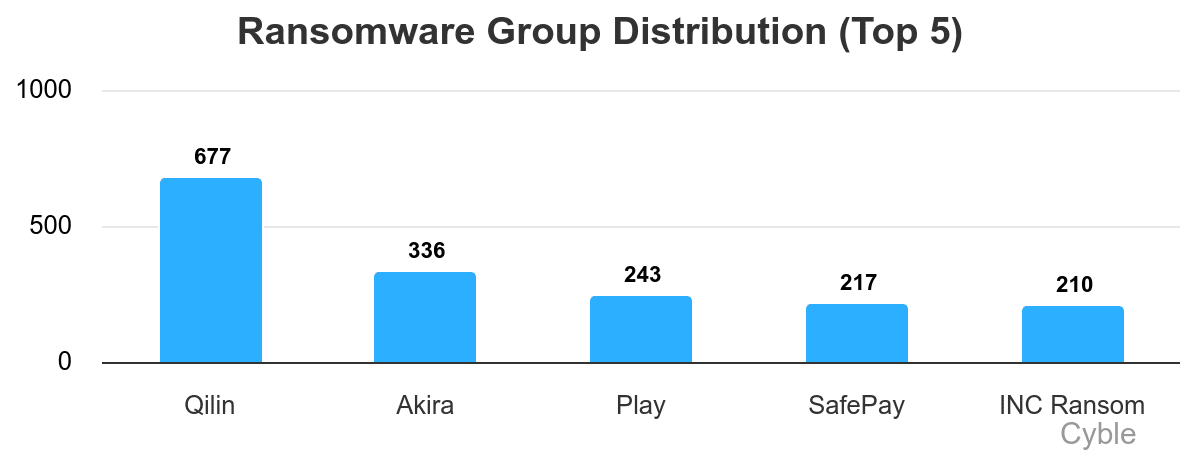
Cyble threat intelligence researchers have documented 677 ransomware attacks by Qilin since the group emerged as the top ransomware group following the decline of RansomHub in what may have been an act of sabotage. Those 677 attacks are more than double those of second-place Akira (chart below).
Qilin Ransomware Group Deploys Linux Ransomware on Windows
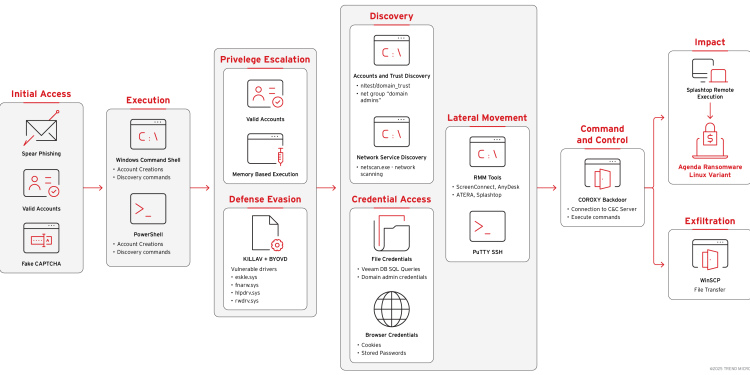
The Qilin ransomware attack documented by Trend Research combined WinSCP for secure file transfer and Splashtop Remote for executing the Linux ransomware binary on Windows machines, in addition to using Bring Your Own Vulnerable Driver (BYOVD) for defense evasion and deployment of multiple SOCKS proxy instances to obfuscate command-and-control (C&C) traffic
Qilin installed legitimate tools like AnyDesk through Atera’s remote monitoring and management (RMM) platform and ScreenConnect for command execution. The attackers also targeted Veeam backup infrastructure using custom credential extraction tools, “systematically harvesting credentials from multiple backup databases to compromise the organization’s disaster recovery capabilities before deploying the ransomware payload,” the researchers said.
“This attack challenges traditional Windows-focused security controls,” the researchers wrote. “The deployment of Linux ransomware on Windows systems demonstrates how threat actors are adapting to bypass endpoint detection systems not configured to detect or prevent Linux binaries executing through remote management channels.”
Initial access appears to have come from a social engineering campaign involving fake CAPTCHA pages, because investigators “identified that multiple endpoints within the compromised environment had connected to malicious fake CAPTCHA pages hosted on Cloudflare R2 storage infrastructure. These pages presented convincing replicas of legitimate Google CAPTCHA verification prompts.”
Those pages apparently delivered infostealers to the endpoints, harvesting authentication tokens, browser cookies, and stored credentials.
“The presence of valid credentials used throughout the attack chain strongly suggests that these stolen credentials provided the … threat actors with the valid accounts necessary for their initial access into the environment,” the researchers said. “This assessment is further supported by the attackers’ ability to bypass multifactor authentication (MFA) and move laterally using legitimate user sessions, indicating they possessed harvested credentials rather than relying on traditional exploitation techniques.”
The attackers used a SOCKS proxy DLL for remote access and command execution, loaded directly into memory using the legitimate Windows rundll32.exe process. The legitimate administrator account password was also reset to prevent admins from regaining access.
ScreenConnect was used to execute discovery commands via temporary command scripts, “systematically enumerating domain trusts and identifying privileged accounts while appearing as normal administrative activity.”
Network scanning tools like NetScan were also used to discover additional systems, services, and potential lateral movement targets, while PuTTY SSH clients were used to facilitate lateral movement to Linux systems within the environment.
Qilin Targeting Veeam Backups to Harvest Credentials
The Qilin attackers targeted Veeam backup infrastructure to harvest credentials, “recognizing that backup systems often store credentials for accessing multiple systems across the enterprise,” the Trend researchers said.
PowerShell scripts with base64-encoded payloads were used to extract and decrypt stored credentials from Veeam databases.
“When decoded, these scripts revealed systematic targeting of multiple Veeam backup databases, each containing credentials for different segments of the infrastructure,” the researchers said. “This approach provided the attackers with a comprehensive set of credentials for remote systems, domain controllers, and critical servers stored within the backup infrastructure.”
Qilin Defense Evasion Tactics
The attackers deployed “sophisticated anti-analysis tools to evade security solutions,” Trend said, with 2stX.exe and Or2.exe using the eskle.sys driver for anti-antivirus capabilities through a BYOVD attack. The eskle.sys driver was used to disable security solutions, terminate processes, and evade detection, they said.
Cisco Talos researchers documented Qilin defense evasion techniques that included using obfuscated PowerShell code that employed numeric encoding.
Executing the PowerShell commands makes three configuration changes, the Talos researchers said. Disabling Windows Antimalware Scan Interface (AMSI) prevents interference with execution of payloads, and disabling TLS certificate validation allows the attackers to contact malicious domains or C2 servers.
The third configuration change enables Restricted Admin to force RDP authentication to rely on NT hashes or Kerberos tickets rather than passwords. “Although passwords are not retained, NT hashes remain on the system and can be abused by an attacker to impersonate the user,” Talos said.
The Talos researchers observed “traces of attempts to disable EDR using multiple methods,” such as commands that launch the EDR’s uninstall.exe file or attempts to stop services using the sc command. Use of open source tools like dark-kill and HRSword was also observed.
“The use of legitimate tools and cross-platform execution methods makes detection significantly more challenging,” the Trend researchers said. “Organizations must urgently reassess their security posture to account for these unconventional attack vectors and implement enhanced monitoring of remote management tools and backup system access.”