The notorious HelloKitty ransomware has rebranded itself as HelloGookie ransomware. This transformation is accompanied by strategic maneuvers and community engagement that shed light on the adaptability and agility of this ransomware operator.
This rebranding comes with more than just a change in name; it signifies a shift in tactics and possibly a response to the competitive environment within the cybercriminal community. HelloGookie’s emergence was accompanied by the release of decryption keys and the establishment of a new blog, signaling a proactive approach to engaging with potential victims.
HelloKitty Ransomware Rebranded to HelloGookie Ransomware

Behind the scenes, the creator behind HelloGookie, known simply as Gookee/Gookie, has made strategic overtures to the LockBit ransomware group. This gesture, while seemingly diplomatic, hints at a desire to avoid direct competition and potentially collaborate for mutual benefit.
Such an alliance highlights the collaborative nature of ransomware groups, where operators navigate a fine line between cooperation and rivalry. Moreover, Gookie’s successful reclamation of their account on the Exploit forum further represents the shift in technology and authority in the ransomware group where the group has claimed credibility over the years.
The forum serves as a hub for cybercriminal activity, facilitating discussions, collaboration, and the exchange of tools and techniques. Gookie’s return to the forum also represents a resurgence in their activities and potentially newly added victims.
Forum Conversations Reveals HelloGookie’s Plan

Forum conversations provide insights into HelloGookie’s tactics and capabilities. Updates targeting both Linux and Windows systems suggest a commitment to expanding its reach across diverse platforms. Additionally, calls for collaboration and the recruitment of individuals with access to high-value targets indicate a strategic shift towards more sophisticated and lucrative operations.
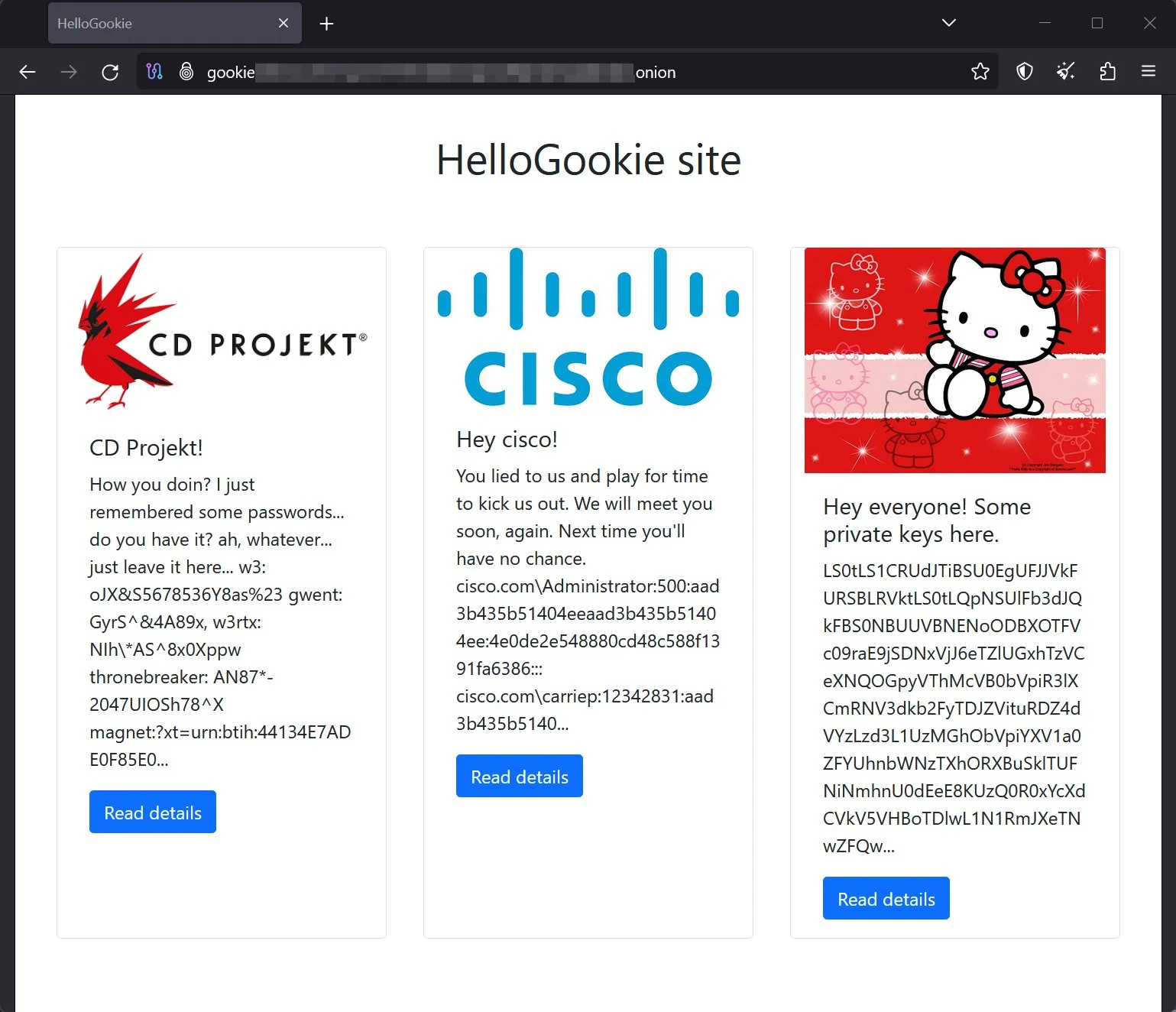
The HelloGookie website further highlights the ransomware’s impact, listing new victims and showcasing the breadth of its reach. From prominent organizations like CD PROJEKT to industry giants like CISCO, the ransomware group has started expanding its reach to various sectors.
The passwords for leaked encrypted source code archives, including Witcher 3 and Thronebreaker, previously priced at $10k each, are also available on the new data leak site. The divulgence of private keys adds another layer of complexity wherein the threat actor is openly sharing private keys on its blog, commencing new levels of threat for the affected parties.
The original HelloKitty ransomware group was identified in 2020, specializing in infiltrating networks, encrypting data, and demanding ransoms. It targets organizations with sensitive data, posing a serious threat to businesses. Now, the threat is bigger and more capable that goes beyond mere encryption and extortion.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.




















































