Apple issued notifications to users in 92 countries on April 11, alerting them of possible mercenary spyware attacks. However, with this update, the Apple state-sponsored notification signals a notable shift in its threat notification policy.
The tech giant has opted to omit the term “state-sponsored” from its alerts, replacing it with the phrase “mercenary spyware attacks.” This adjustment announced through an update on April 10, has caught the attention of users globally.
Previously, Apple had used the term “state-sponsored” to warn users of potential malware threats. However, the recent update acknowledges cybersecurity threats, specifically highlighting the menace of hacker groups.
The company emphasized that while these cyberattacks have historically been associated with state actors, including private entities developing spyware like the NSO Group’s Pegasus, the term now encompasses a broader spectrum of potential threats.
Apple State-Sponsored Alert Swaps With “Mercenary Spyware Attacks”
The change became evident when Apple issued notification letters to users about possible intrusions by “mercenary spyware attacks”. This shift follows reported pressure from the Indian government regarding the association of cybersecurity breaches with state actors. Last year, Apple’s alerts to opposition leaders in India sparked controversy, prompting discussions between the tech giant and Indian officials.
The alteration in terminology is a response to the rising threats of hacker groups and the need for nuanced responses. By replacing “state-sponsored” with “mercenary spyware attack,” Apple aims to provide more accurate and comprehensive threat notifications to its users.
Talking about these hacker groups, Apple says, “Mercenary spyware attacks cost millions of dollars and often have a short shelf life, making them much harder to detect and prevent. The vast majority of users will never be targeted by such attacks.”
Moreover, the tech giant has devised methods when it detects activity indicative of a mercenary spyware attack. In such a situation, affected users receive notifications through two channels: a Threat Notification displayed upon signing in to appleid.apple.com and email/iMessage notifications sent to their associated contact details.
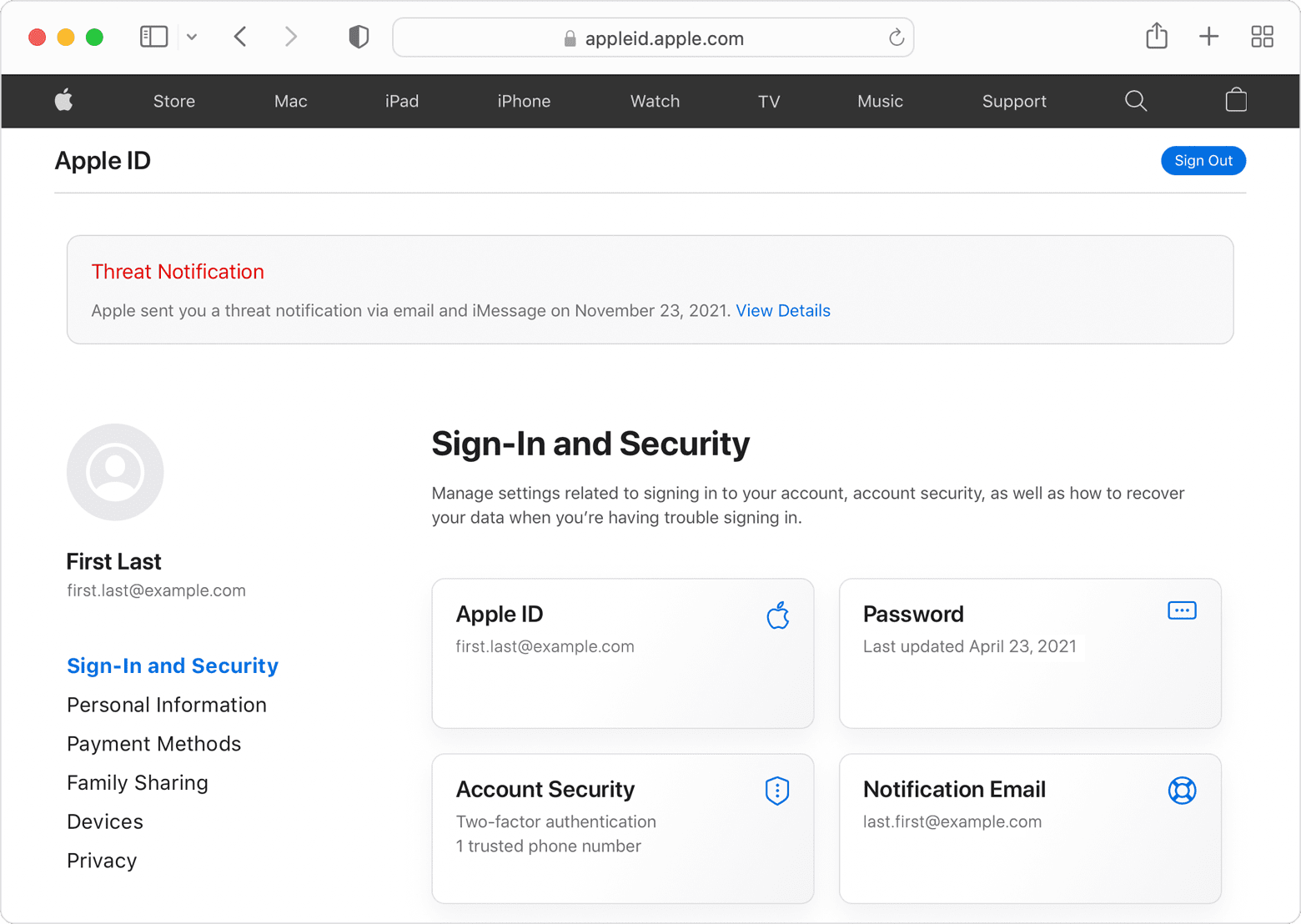
These notifications provide additional steps, such as enabling Lockdown Mode, to enhance device security. Recipients of Apple threat notifications are advised to seek expert assistance, such as the Digital Security Helpline provided by Access Now, available 24/7 for tailored security advice.
The Apple Apple State-Sponsored Controversy
The controversy surrounding Apple state-sponsored notifications dates back to October of the previous year when several Indian opposition leaders reported receiving alerts about state-sponsored attackers attempting to compromise their iPhones.
These claims led to a standoff between Apple and the Indian government, with the Ministry of Electronics and Information Technology (MeitY) seeking clarification from the tech company, as reported by Times of India.
Despite the government’s inquiries, Apple remained somewhat ambiguous in its responses, highlighting the inherent complexities in addressing vulnerabilities in proprietary platforms.
Minister of State for IT, Rajeev Chandrasekhar, emphasized the importance of clarity regarding device vulnerabilities, reflecting the ongoing dialogue between governments and tech companies regarding cybersecurity.
In light of these developments, The Cyber Express has also reached out to Apple to learn more about the replacements of the term state-sponsored to mercenary spyware attacks. However, at the time of writing this, no official statement or response has been received.
Apple asserts that since enabling the threat notification feature in late 2021, it has sent alerts to users in nearly 150 countries, highlighting the need to ensure user safety and security. This proactive approach aligns with the company’s ongoing efforts to counter global cyberattacks targeting iPhone users.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.